Security Camera Input Setup
1. NVR/DVR (remote or local)
Camera / DVR / NVR Alarm Input
1. Trigger video recording on the camera associated with the alarm.
1. Capture a still image snapshot.
The inputs and outputs can be used to eliminate unnecessary recording of
video or coincide with your alarm system to systematically create a reliable
and accountable security source. When input and output mechanisms are
triggered, you can (manually or automatically) request through the network
video device that certain actions be performed over the network as well as
trigger devices attached to the output ports. Example:
This example picture above shows a person interrupting a sensors function. This creates a signal that travels to the camera and the camera computes the message. The camera then functions as programmed and starts recording (snapshots or footage) to the delegated device while simultaneously triggers a relay to close. When the relay closes, it completes the circuit for the siren or strobe to activate. Another configuration (as long as the cameras capable), have the camera record to the desired method based on motion and simultaneously trigger the relay to set off the siren. In this example, a motion sensor is taken out of the equation.
|
Device Type |
Description |
Occurrence of activation |
|
Entry Contacts |
Simple magnetic sensors detecting
opening of doors, windows, gates and shutters. |
When the circuit is broken (door is
opened) the camera can record and/or send a snapshot and notifications |
|
Motion Sensors |
A sensor that detects motion either
based on heat, light, or frequency |
When motion is detected, the sensor
breaks the circuit and the camera can record and/or send a snapshot and
notifications |
|
Glass Break or Glass Shock Sensor |
A sensor capable of distinguishing
the sound/vibration of breaking glass and/or splintering wood. |
When glass is disturbed or
shattered, the glass sensor breaks the circuit and the camera can record
and/or send a snapshot and notifications |
|
Pressure strip or switch |
A pressure or switch sensor that
are needed to interact with before gaining entry or exiting a premise or
structure |
When the sensor is triggered it
breaks the circuit and the camera can record and/or send a snapshot and
notifications |
Installing a
motion detector and integrating it with a security camera system is fairly
simple. CCTV Camera Pros supports professional and DIY installers. Most PIR
motion sensors are 12V DC powered which gives installers the choice of using a
individual 12V DC power supply or one of the ports on a multi-channel power
supply box (the same ones used with security cameras).
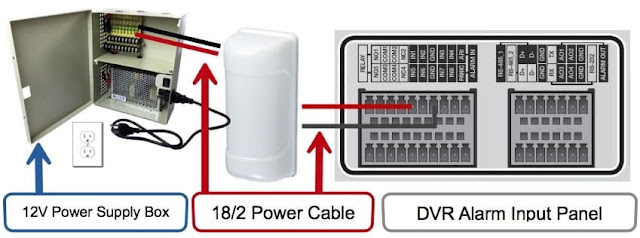
In this
first diagram, a single 12V DC power transformer is used. This is how
it works.
1.
On
the right side of the diagram, the alarm input / output panel of the DVR is
shown. This is what the alarm panel on the back.
2.
18/2
gauge power cable connects the output of the motion detector to one of the
alarm input ports on the DVR.
3.
18/2
gauge power cable is also used to connect the motion detector to an individual
DC power supply.
4. A PT-4 power lead connects the raw cables to the 3.1mm plug on the power supply.
Installation
with Power Supply Box
A multi-channel
power supply box can be used instead of an individual power supply.
Here are some
frequently asked questions about integrating PIR motion detectors with security
camera systems.
·
How
are motion detectors used with security camera systems?
The most common way to integrate a motion detector with a security camera
system is to hard wire the motion detector to the same surveillance DVR that
your security cameras are connected to. You must make sure that your DVR that
has alarm inputs.
·
Can I just use motion detected from my
security camera instead of an external motion sensor?
Yes, most DVRs support video motion detection triggered by cameras. Please note
that this is different from PIR (passive infrared) motion detection and can be
less reliable. Video motion detection tends to produce more false positives
than PIR motion detection, especially in outdoor and infrared camera
applications. This is because the video tends to be more noisy and outdoor
environments tend to always have some motion from wind and other natural
elements.
·
What type of cable is used to wire
motion detectors to DVRs?
The following types of cable can be used to wire motion detectors: CAT-5
cable (one pair), 18/2 conductor power cable.
·
Do motion detectors require power?
Yes. Most PIR motion detectors use 12V DC power. All of ours include the proper
power supply with them.
·
Can I use multiple motion detectors
with my surveillance system?
Yes, as long as your DVR has multiple alarm input ports, you can use multiple
motion detectors. Different model DVRs support different numbers of alarm
inputs so consult the specification or contact us if you need help.
Not every camera or NVR/DVR possesses
this unique features or can be operated through the above mentioned methods. Be
sure you research everything you will need to make this type of setup
successfully work for you. This includes the correct relays, power supplies,
capable camera and recording devices. Most our IP mega pixel cameras and
recorders have the capability of all previous mention features above.
If you are
not understand, you can touch with us for further support. We deal Infinova, Hanwha,
Milestone, Mirasys & Luxriot brand.