GUIDE TO BUILDING AUTOMATION
Building automation is monitoring and controlling a
building’s systems including: mechanical, security, fire safety, lighting,
heating, ventilation, and air conditioning.
Such systems can
- ·
keep
building climates within a specified range,
- ·
light
rooms according to an occupancy schedule,
- ·
monitor
performance and device failures in all systems, and
- ·
alarm
facility managers in the event of a malfunction.
Relative to a non-controlled building, a building with
a BAS has lower energy and maintenance costs.
There are many components to a building automation
system that require a little explaining to understand, and the benefits of
installing such a system may not be immediately clear until you understand the
mechanisms driving these systems.
That’s why we created this ultimate guide to
understanding building automation systems. It’s designed to be an easy
read-through, but feel free to use the links below to go directly to a topic
that is relevant to your own research.
WHAT
IS BUILDING AUTOMATION?
Building automation most broadly
refers to creating centralized, networked systems of hardware and software
monitors and controls a building’s facility systems (electricity, lighting,
plumbing, HVAC, water supply, etc.)
When facilities are monitored and
controlled in a seamless fashion, this creates a much more reliable working
environment for the building’s tenants. Furthermore, the efficiency introduced
through automation allows the building’s facility management team to adopt more
sustainable practices and reduce energy costs.
These are the four core functions of
a building automation system:
·
To
control the building environment
·
To
operate systems according to occupancy and energy demand
·
To
monitor and correct system performance
·
To
alert or sound alarms when needed
At optimal performance levels, an
automated building is greener and more user-friendly than a non-controlled
building.
A Building Automation System may be denoted as:
An automated system where building services, such as utilities, communicate with each other to exchange digital, analogue or other forms of information, potentially to a central control point.
An automated system where building services, such as utilities, communicate with each other to exchange digital, analogue or other forms of information, potentially to a central control point.
What Is Meant By ‘Controlled?
A
key component in a building automation system is called a controller, which is
a small, specialized computer. We will explore exactly how these work in a
later section. For now, it’s important to understand the applications of these
controllers.
Controllers
regulate the performance of various facilities within the building. Traditionally,
this includes the following:
·
Mechanical
systems
·
Electrical
systems
·
Plumbing
systems
·
Heating,
ventilation and air-conditioning systems
·
Lighting
systems
·
Security
Systems
·
Surveillance
Systems
A
more robust building automation system can even control security systems, the
fire alarm system and the building’s elevators.
To
understand the importance of control, it helps to imagine a much older system,
such as an old heating system. Take wood-burning stoves, for example. Anyone
heating their buildings through pure woodfire had no way to precisely regulate
the temperature, or even the smoke output. Furthermore, fueling that fire was a
manual effort.
Fast-forward
150 years: Heating systems can be regulated with intelligent controllers that
can set the temperature of a specific room to a precise degree. And it can be
set to automatically cool down overnight, when no one is in the building.
The
technology that exists today allows buildings to essentially learn from itself.
A modern building automation system will monitor the various facilities it
controls to understand how to optimize for maximum efficiency. It’s no longer a
matter of heating a room to a specific temperature; systems today can learn who
enters what rooms at what times so that buildings can adjust to the needs of
the tenants, and then conserve energy when none is needed.
There
is a growing overlap between the idea of controlling a building and learning
from all the data the system collects. That’s why automated buildings are
called “smart buildings” or “intelligent buildings.” And they’re getting
smarter all the time.
THE
EVOLUTION OF SMART BUILDINGS
Kevin Callahan, writing for
Automation.com, points to the creation of the incubator thermostat — to keep
chicken eggs warm and allow them to hatch — as the origin of smart buildings.
Like most technologies, building
automation has advanced just within our lifetimes at a rate that would have
baffled facility managers and engineers in, say, the 1950s. Back then,
automated buildings relied on pneumatic controls in which compressed air was
the medium of exchange for the monitors and controllers in the system.
By the 1980s, microprocessors had
become small enough and sufficiently inexpensive that they could be implemented
in building automation systems. Moving from compressed air to analog controls
to digital controls was nothing short of a revolution. A decade later, open
protocols were introduced that allowed the controlled facilities to actually
communicate with one another. By the turn of the millennium, wireless
technology allowed components to communicate without cable attachments.
An
Intelligent Building system may be denoted as:
An automated system where building services and corporate
processes, communicate with each other to exchange digital, analogue or other
forms of information, to a central control point to manage the environment.
Terms to Understand
At first, the terms building
automation professionals use look like a big game of alphabet soup. There are
acronyms everywhere. Let’s clarify this now:
Building Management
System (BMS) and Building Control System (BCS) — These are more general terms
for systems that control a building’s facilities, although they are not
necessarily automation systems.
Building Automation
System (BAS) —
A BAS is a subset of the management and control systems above and can be a part
of the larger BMS or BCS. That said, building management and building
automation have so thoroughly overlapped in recent years that it’s
understandable people would use those terms interchangeably.
Energy Management
System (EMS) and Energy Management Control System (EMCS)— These are systems that
specifically deal with energy consumption, metering, etc. There is enough
overlap between what a BAS does and what an EMS does that we can consider these
synonymous.
Direct Digital Control
(DDC) — This
is the innovation that was brought about by small, affordable microprocessors
in the ‘80s. DDC is the method by which the components of a digital system
communicate.
Application
Programming Interface (API) —
This is a term common in computer programing. It describes the code that
defines how two or more pieces of software communicate with one another.
What makes the terminology
particularly complicated is that the technology evolves so quickly that it’s
hard to know at what point a new term needs to be applied. Then, you also have
professionals in different countries using different terms but still having to
communicate with one another. Just be prepared for the terminology to be in a
state of flux.
HOW
DO BUILDING AUTOMATION SYSTEMS WORK?
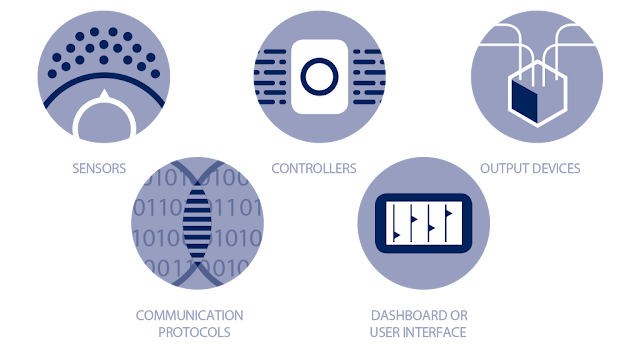
Basic BAS have five essential
components:
Input devices / Sensors — Devices that measure values
such as CO2 output, temperature, humidity, daylight or even room occupancy.
Controllers — These are the brains of the
systems. Controllers take data from the collectors and decide how the system
will respond.
Output devices — These carry out the commands
from the controller. Example devices are relays and actuators.
Communications
protocols —
Think of these as the language spoken among the components of the BAS. A
popular example of a communications protocol is BACnet.
Dashboard or user
interface —
These are the screens or interfaces humans use to interact with the BAS. The
dashboard is where building data are reported.
What a BAS Can Do
·
It
can set up the lighting and HVAC systems to operate on a schedule that makes
those systems both more intelligent and more efficient.
·
It
can get the various components and facilities within a building to coordinate
and work together toward greater overall efficiency.
·
It
can optimize the flow of incoming outside air to regulate freshness,
temperature and comfort inside the building.
·
It
can tell you when an HVAC unit is running in both heating and cooling helping
to reduce utility costs.
·
It
can know when an emergency such as a fire breaks out and turn off any
facilities that could endanger building occupants.
·
It
can detect a problem with one of the building’s facilities — such as, for
example, an elevator getting stuck with people inside — and send an instant
message or an email to the building’s facility manager to alert him/her of the
problem.
·
It
can identify who and when someone is entering and leaving a building
·
It
can turn a camera on a begin recording when activity takes place – and send an
alert and direct camera feed to the security team and facility manager.
·
Are
there other functions that address clear pain points for building owners /
facility managers?
The Role of
Controllers
Controllers are the brains of the
BAS, so they require a little more exploration. As mentioned above, the advent
of direct digital control modules opened up a whole universe of possibilities
for automating buildings.
A digital controller can receive
input data, apply logic (an algorithm, just as Google does with search data) to
that information, then send out a command based on what information was
processed. This is best illustrated through the basic three-part DDC loop:
1. Let’s say a sensor detects an
increase in temperature in a company’s board room when the room is known to be
unoccupied.
2. The controller will apply logic
according to what it knows: That no one is expected in that room, thus there is
no demand for additional heat, thus there is no need for that room to warm up.
(Note: The algorithm with which a controller processes information is actually
far more complex than depicted in this example.) It then sends a command to the
heating system to reduce output.
3. The actual heating unit for the
boardroom in question receives that command and dials back its heat output. All
of this appears to happen almost instantaneously.
WHY
ARE BUILDING AUTOMATION SYSTEMS USEFUL?
The
benefits of building automation are manifold, but the real reasons facility
managers adopt building automation systems break down into three broad
categories:
·
They
save building owners money
·
They
allow building occupants to feel more comfortable and be more productive
·
They
reduce a building’s environmental impact
Saving Money
The place where a BAS can save a
building owner a significant amount of money is in utility bills. A more
energy-efficient building simply costs less to run.
An automated building can, for
example, learn and begin to predict building and room occupancy, as
demonstrated earlier with the heated board room example. If a building can know
when the demand for lighting or HVAC facilities will wax and wane, then it can
dial back output when demand is lower. Estimated energy savings from simply
monitoring occupancy range from 10-30%, which can add up to thousands of
dollars saved on utilities each month.
Furthermore, a building can also
sync up with the outdoor environment for maximum efficiency. This is most
useful during the spring and summer, when there is more daylight (and thus less
demand for interior lighting) and when it is warmer outside, allowing the
building to leverage natural air circulation for comfort.
Data collection and reporting also
makes facility management more cost efficient. In the event of a failure
somewhere within the system, this will get reported right on the BAS dashboard,
meaning a facility professional doesn’t have to spend time looking for and
trying to diagnose the problem.
Finally, optimizing the operations
of different building facilities extends the lives of the actual equipment,
meaning reduced replacement and maintenance costs.
Typically, facility managers find
that the money a BAS saves them will over time offset the installation and
implementation of the system itself.
Comfort and
Productivity
Smarter control over the building’s
internal environment will keep occupants happier, thereby reducing complaints
and time spent resolving those complaints. Furthermore, studies have shown that
improved ventilation and air quality have a direct impact on a business’s bottom
line: Employees take fewer sick days, and greater comfort allows employees to
focus on their work, allowing them to increase their individual productivity.
Environmentally
Friendly
The key to an automated building’s
reduced environmental impact is its energy efficiency. By reducing energy
consumption, a BAS can reduce the output of greenhouse gases and improve the
building’s indoor air quality, the latter of which ties back into bottom-line
concerns about occupant productivity.
Furthermore, an automated building
can monitor and thus control waste in facilities such as the plumbing and
wastewater systems. By reducing waste through efficiencies, a BAS can leave an
even smaller environmental footprint. In addition, a regulatory government
agency could collect the BAS’s data to actually validate a building’s energy
consumption. This is key if the building’s owner is trying to achieve LEED or
some other type of certification.
The fact that everything is integrated into one control
system, instead of three separate systems, is a real positive – Arindam Bhadra,
Technical Head, SSA Integrate.
Sources