Fire safety professionals
constantly seek the benefits of early warning of potential fires. In a perfect
world it would be possible to place hundreds of smoke detecting sensors above
and around any items or areas at risk. This would certainly enable a fast
response to a potential fire, saving valuable time even in voluminous areas or
where a high airflow may be present. But of course such a dream is not possible
from a practical or financial point of view.
Video smoke detection
technology makes this dream a reality.
Video smoke (VISD) and flame detection (VIFD) is performed
by a software algorithm running on Visual Signal Processors (ViSPs) that
implement parallel processing engines in hardware. Video images are analysed in
real time by applying digital image processing techniques that allows smoke and
flames to be detected with a high degree of confidence. The video image is
continually monitored for changes and false alarms are eliminated by
compensating for camera noise and acquiring knowledge of the camera view over
time.
 |
| an illustration of how the Video Smoke Detection
process works |
Multiple zones can be defined for a camera view in which
smoke and flames are to be detected. Each zone has a set of parameters that
provide complete control over the detection algorithm. These parameters are
configured individually for each zone in order to cater for a wide variety of
application scenarios. It is also possible to combine information from multiple
cameras to enhance the detection process.
Stemming from many years of research and development several
complex statistical and geometrical measurements are made on the video image
data from each zone as dictated by the control parameters. This is made
possible by the parallel digital signal processing capabilities of the
hardware. The scale of parameter settings is such that it is possible to detect
smoke ranging from slow emerging faint smoke through to dense smoke plumes that
are produced in a short period of time.
Once the measurements have been made from the video image
data a set of rules can be applied to determine if they characterise smoke or
flames. The rules can also be tuned to meet the specific application
requirements to complete a robust and successful detection algorithm.
VSD/VID (VISD) is based on sophisticated computer analysis
of the video image seen by the CCTV camera (sensor). Using advanced
image-processing technology and extensive detection algorithms (and known false
alarm phenomena); the VID can automatically identify the distinctive
characteristics of smoke patterns. The fire detection industry has an abundance
of known smoke signatures and these are built into the system to give an
accurate decision on whether smoke is present.
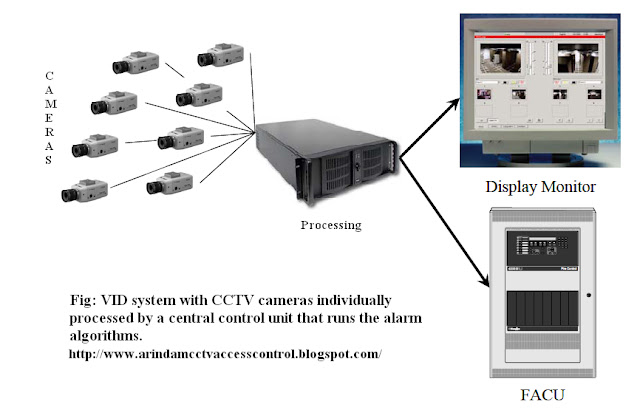
The VSD system uses standard CCTV equipment linked to a self
contained processing system which is capable of recognising small amounts of
smoke within the video image and alerting the system operator both at the
processor and by a variety of remote outputs.
The VSD system employs highly complex algorithms to process
video information from CCTV cameras simultaneously. The video hardware is
designed to allow simultaneous real time digitising of all images, which means
that the system does not multiplex images and, therefore, no information is
lost or delayed. All alarm condition images are logged, time & date
stamped, and stored within the system’s memory.
The VSD system detects smoke rapidly by looking for small
areas of change within the image at the digitisation stage and only passing
these pixel changes to the main processor for further filtering.
The video information is passed through a series of filters,
which seek particular characteristics that can be associated with smoke behavior.
Further analysis is then carried out on the relationships between the filtered
characteristics to determine whether all the conditions have been met for the
system to confidently predict the presence of smoke.
The system installer has the ability to vary the amount of
smoke signal, and the length of time that the smoke exists before an alarm
condition is raised to cater for situations where there may be background smoke
present. The installer may also divide the video image into up to 16 zones and programmed
the system to alarm only if smoke is present in multiple zones. Each zone can
also be separately configured to generate an alarm at different levels of smoke
activity.
The performance of a Smoke or Flame VID system must take
into account three general items:
1. Fire sources
2. Environment
3. System variables
Standard smoke detection systems, be they point detection
systems, infra-red beam detectors or aspirating systems all require the smoke
generated from any combustion to reach them before they can recognise the
particulates and activate an alarm. Such systems can function very effectively
in internal thermally stable environments with low to moderate ceiling heights.
In large volumeous spaces such as enclosed sports arenas,
exhibition halls, aircraft hangers and atriums, solar radiation, air
conditioning systems and translucent glass all contribute to an increasing
ambient temperature from floor to ceiling, known as a thermally stratified
environment.
In a smouldering fire or low energy flaming fire scenario
the raising combustion products cool as they rise through the air and move
further away from the centre of combustion. In a temperature-stratified
environment the ambient air temperature increases with height. As the
combustion plume rises it cools, if this cooling reaches equilibrium with the
temperature of the ambient air the smoke products will loose their buoyancy and
move laterally to produce a roughly horizontal layer. If the temperature
slowly increases the hot air above the smoke will expand thus further reducing
the height of the smoke stratification layer.
In environments with a high percentage change of air caused
by either high velocity air-conditioning (HVAC) systems, or large open doors,
smoke particles generated during low energy combustion can become quickly
dispersed or diluted to the point where there are insufficient concentrations
to activate an alarm in a standard smoke detection system.
These twin problems of stratification and dilution can
seriously delay or even prevent a smoke detection system from entering an alarm
state.
VSD systems over come both of these phenomena by looking
below any stratification or dilution boundary at the incept point of any
potential fire and identifying smoke generation at or very close to the source.
So, be separately configured to generate an alarm at
different levels of smoke activity.
In general, VSD
systems do not have fixed settings. They have many parameters that need to be
adjusted to provide the optimum response to a specific fire risk. Therefore, it
is very important that the manufacturer should be fully consulted in matters of
product application and system design. The manufacturer’s installation,
commissioning and service and maintenance instructions should also be followed.
The location and spacing of detectors shall be based on the
principle of operation and an engineering survey of the conditions anticipated
in service. The manufacturer’s published instructions shall be consulted for
recommended detector uses and locations. an engineering evaluation that
includes the following:
(1) Structural features, size, and shape of the rooms and
bays
(2) Occupancy and uses of the area
(3) Ceiling height
(4) Ceiling shape, surface, and obstructions
(5) Ventilation
(6) Ambient environment
(7) Burning characteristics of the combustible materials
present
(8) Configuration of the contents in the area to be
protected
The National Fire Alarm Code, NFPA 72-2007, recognizes the
use of flame and smoke VID systems. (5.7.6 Video Image Smoke Detection; 5.8.5
Video Image Flame Detection) Per the Code, the installation of these
systems requires a performance-based design. There are no prescriptive sitting
requirements. Flame VID systems are classified as radiant energy sensing fire
detectors and are treated similar to optical flame detectors. Due to the
variability of VISD system capabilities and the differences in alarm algorithm
technologies, NFPA 72 requires that the systems be inspected, tested, and maintained
in accordance with the manufacturer’s published instructions.
Currently, there are no systems that are UL listed, and
there is no UL standard that specifically addresses VID/VSD systems. Four
systems have been FM approved. These include a system that detects only smoke,
one that detects only flame and two that detect both. The systems have been
approved to meet the requirements of FM Standard 3260, Radiant Energy- Sensing
Fire Detectors for Automatic Fire Alarm Signaling, and UL 268, Smoke Detectors
for Fire Alarm Signaling Systems.
The effect of all the changeable parameters in the VSD, such
as camera lenses, software parameters adjustment and lighting conditions should
be taken into consideration following the consultation principle given in BS5839
Part 1: 2002, clause 6.
BS 5839-1:2002 recognises the existence of VSD. Clause 21 j)
recommends that:
"Video smoke detection systems should be capable of
detecting smoke reliably in the absence of the normal lighting in the building
and the absence of the mains power supply to any lighting provided specifically
to aid the detection of smoke."
The foundational information collected for identifying
typical/standard fire and smoke scenarios, likely false/nuisance scenarios, and
a range of ambient conditions to which VISD systems may be subjected in the
three target applications. This work included researching and reviewing fire
incident data and conducting an industry workshop on VISD technology. On-site
surveys and interviews with end-users were also conducted.
Installation cables should be in accordance with the
recommendations of BS 5839-1:2002.
A VSD detecting fires in certain large open areas and areas
of special high risk as:
1. VSD systems can be used for outdoor applications, such as
train stations and off-shore oil platforms.
2. The ability of VSD to be programmed to provide different
sensitivity (range) by lens selection, and to adapt to difficult application
environments (false alarm sources) by tuning software operational parameters,
makes it an ideal detection tool in special applications where an engineered
solution is likely to give the best answer.
3. The ability to protect a large area, and/or areas with
excessive ceiling heights, while still achieving fast detection. With VSD,
smoke in the camera field of view can be detected whereas with other detector
types, smoke has to migrate to, and be present in, the sensing area e.g. the
sensing beam of a beam detector or the sensing chamber of a point smoke
detector.
4. VSD, by providing accurate location of the incident, will
benefit applications where targeted fire protection measures are required.
5. The ability to have live video immediately available upon
detecting a pre-alarm or an alarm condition. This immediate situational
awareness allows monitoring personnel to easily view the protected area to
determine the extent of the fire and to more accurately identify the location.
6. Archiving of still and video images associated with alarm
conditions also provides a means of assessing the cause of incidents and
provides a basis for changes in the detection system if the event was a
false/nuisance alarm.
7. The ability to sub-divide the image into different areas
for separately identifying fire risks or programming out (masking) known
sources of potential false alarms.
8. VSD, by providing visual verification of the event, will
give operators information to facilitate a better and faster structured response
of an incident and enable safer investigation by remote viewing.
It is important to always follow the manufacturer’s
recommendations for testing, servicing, maintenance and replacement
requirements. It may be desirable that, in some installations where the effect
of potential false alarm sources cannot be fully determined, a period of trial
is undertaken before completing the commissioning of the system and handing it
over to the client.
A method, appropriate to the risk, of testing the
effectiveness of the VSD at both the commissioning stage and at subsequent
service and maintenance visits should be agreed with the equipment
manufacturers or system installer. Tests should be conducted and documented in accordance
with this method.
1. Where certain processes are likely to produce smoke-like
images which may be misunderstood by the video analysis software, unless it has
been demonstrated through trial and, if required, tuning of the equipment so
that the effect of these false alarm sources have been adequately established
and eradicated. Examples include processes generating large amounts of steam
and/or other gas plumes (exhaust fumes from forklift trucks) and/or
environmental pollutants (vapour, dust, sprays). In outdoor or semi-outdoor
situations this may also include insect swarms.
2. Where a deterministic response to known fires is required
and can be achieved by the use of EN 54 approved detectors, i.e. most standard
commercial and industrial applications.
3. Where there is a danger that the ambient lighting level
is either too low or too high to obtain a satisfactory response from the VSD at
the time it is required to monitor the risk, unless specific provisions are
available to alleviate this danger. For example infrared illumination of the
scene with back-up power supply, polarized lens filters, or where very intense
light sources can blind the camera.
4. Where there are significant obstructions in the camera
line-of-sight of the main identified risk or where such obstructions are
temporary and of an unpredictable nature.
5. Where a particular equipment configuration, including
installation cables, would not assure the integrity of the alarm transmission
path through the system so as to provide the desired warnings to the occupants
of a building or the desired response from the emergency services.
6. Where likely environmental conditions present may have an
adverse effect on the ability of the VSD to properly operate. For example this
would include fog, mist, snow and rain.
7. Where the use of
cameras is not appropriate due to data protection issues.