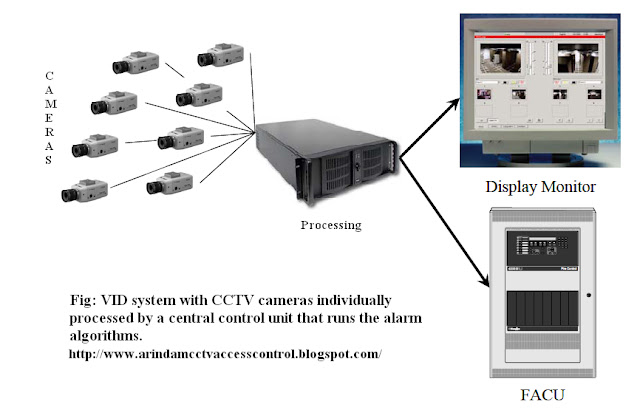
CCTV cameras are available with various voltage
requirements. These include 12VDC, 24VAC, and 115/230VAC. 115/230V models are
rarely used, due to the expense of providing local high-voltage power. 24VAC
models are quite common in that they can tolerate greater wire distances than
their 12VDC counterparts, and are generally more immune to ground-loops. A
significant portion of cameras today are wide-ranging in that they can operate
on 12VDC or 24VAC.
12VDC Operation
Should the camera operate off of 12VDC only, special considerations must be taken to ensure correct operating voltage. These considerations include short wire runs, thick wire gauge, or slightly increasing the power supply voltage to achieve the correct voltage at the camera. Another consideration is that 12VDC cameras often connect the power supply return lead to the camera’s ground. The result can be that current from the power supply may flow through the shield of the video path, a recipe for ground-loops. For this reason, it is recommended that 12VDC cameras be powered from a local 12VDC supply that has a floating (not grounded) output.
Some products that allow 4-pair UTP wire to be used to deliver camera Power, Video, and if necessary, telemetry Data. Some “cable integrator” pass-through devices that allow the use of an external power supply and RJ45 connectorisation for in-house wiring. This allows for inter-operability with external low voltage power supplies, including those that deliver 12VDC. An example might be a 4 watt 12VDC camera, which is limited to a wire distance of 43ft (13 meters). This is not a particularly impressive distance, but a better solution is listed below after we discuss 24VAC operation.
24VAC Operation
Also in the UTP range are cable integrators that have built-in individually floating 24 or 28 VAC power supplies. The 28 Volt setting allows 24VAC cameras to operate at extended distances over 4-pair UTP wire. Here, a 4 Watt 24VAC camera with a ±10% tolerance can operate up to 1,047ft (319m).
Dual Voltage 24VAC/12VDC Operation
Many 24VAC and 12VDC cameras are specified to be powered from a source that is ±10%, which is a range of 21.6 VAC to 26.4 VAC or 10.8 VDC to 13.2VDC, respectively. To reduce the number of camera models, most camera manufacturers incorporate a switching power supply that will operate comfortably off any voltage from 10.8 to 30 volts AC or DC. These wide-ranging switchers can therefore operate off 24VAC or 28VAC at very long wire distances, allowing cameras to be powered from the head-end control room. This allows for the entire system to operate off of one UPS. Here, a 4 Watt camera can operate off a 28VAC supply but tolerate a voltage of 14 VAC, yielding 1,467 feet (447 meters). A 2.75 Watt camera can go over 2,000ft (600m).
12VDC Cameras Powered from a 24VAC Supply Should the camera not operate over this wide range, consider using Converter the camera to convert from 24VAC to 12VDC. Easily operate off a voltage as low as 12VAC, allowing it to be powered from a 24VAC or 28VAC source. When calculating distance, set the Camera Minimum Voltage parameter to 14V (half the 28VAC value is where we get maximum power transfer), and set the Camera Power parameter to be 10% higher than the camera’s published rating. The camera current should not exceed 400mA. A 4 Watt 12VDC camera can be 1,336ft (407m) away from the power supply. a 2.75 W 12VDC camera can be 1,942ft (592m).
If you are design analog based CCTV projects, consider per camera per power supply. Always power cameras from a local power source such as a small transformer / SMPS. This is a simple way to do it and will require less cable having to be run which may be fine in a small / Big installation. Do not used Multi-Camera power supply, sometimes called a PDU (power distribution unit) to provide power for the cameras.
As an example a camera my show 5W at 24 VAC. How many amps is that? Based on the chart you would divide 5 by 24 for approximately 0.200 amps or 200 mA (milliamps).
If you have 4A Power Supply then see what happend as in below exp:
Also Visit: http://arindamcctvaccesscontrol.blogspot.in/2012/11/voltage-amperage-guide-for-your-cctv.html
12VDC Operation
Should the camera operate off of 12VDC only, special considerations must be taken to ensure correct operating voltage. These considerations include short wire runs, thick wire gauge, or slightly increasing the power supply voltage to achieve the correct voltage at the camera. Another consideration is that 12VDC cameras often connect the power supply return lead to the camera’s ground. The result can be that current from the power supply may flow through the shield of the video path, a recipe for ground-loops. For this reason, it is recommended that 12VDC cameras be powered from a local 12VDC supply that has a floating (not grounded) output.
Some products that allow 4-pair UTP wire to be used to deliver camera Power, Video, and if necessary, telemetry Data. Some “cable integrator” pass-through devices that allow the use of an external power supply and RJ45 connectorisation for in-house wiring. This allows for inter-operability with external low voltage power supplies, including those that deliver 12VDC. An example might be a 4 watt 12VDC camera, which is limited to a wire distance of 43ft (13 meters). This is not a particularly impressive distance, but a better solution is listed below after we discuss 24VAC operation.
24VAC Operation
Also in the UTP range are cable integrators that have built-in individually floating 24 or 28 VAC power supplies. The 28 Volt setting allows 24VAC cameras to operate at extended distances over 4-pair UTP wire. Here, a 4 Watt 24VAC camera with a ±10% tolerance can operate up to 1,047ft (319m).
Dual Voltage 24VAC/12VDC Operation
Many 24VAC and 12VDC cameras are specified to be powered from a source that is ±10%, which is a range of 21.6 VAC to 26.4 VAC or 10.8 VDC to 13.2VDC, respectively. To reduce the number of camera models, most camera manufacturers incorporate a switching power supply that will operate comfortably off any voltage from 10.8 to 30 volts AC or DC. These wide-ranging switchers can therefore operate off 24VAC or 28VAC at very long wire distances, allowing cameras to be powered from the head-end control room. This allows for the entire system to operate off of one UPS. Here, a 4 Watt camera can operate off a 28VAC supply but tolerate a voltage of 14 VAC, yielding 1,467 feet (447 meters). A 2.75 Watt camera can go over 2,000ft (600m).
12VDC Cameras Powered from a 24VAC Supply Should the camera not operate over this wide range, consider using Converter the camera to convert from 24VAC to 12VDC. Easily operate off a voltage as low as 12VAC, allowing it to be powered from a 24VAC or 28VAC source. When calculating distance, set the Camera Minimum Voltage parameter to 14V (half the 28VAC value is where we get maximum power transfer), and set the Camera Power parameter to be 10% higher than the camera’s published rating. The camera current should not exceed 400mA. A 4 Watt 12VDC camera can be 1,336ft (407m) away from the power supply. a 2.75 W 12VDC camera can be 1,942ft (592m).
If you are design analog based CCTV projects, consider per camera per power supply. Always power cameras from a local power source such as a small transformer / SMPS. This is a simple way to do it and will require less cable having to be run which may be fine in a small / Big installation. Do not used Multi-Camera power supply, sometimes called a PDU (power distribution unit) to provide power for the cameras.
So how do you determine the correct CCTV power supply for your security camera system?
There are two main selection criteria.
- The number of cameras to be powered.
- The total current draw.
As an example a camera my show 5W at 24 VAC. How many amps is that? Based on the chart you would divide 5 by 24 for approximately 0.200 amps or 200 mA (milliamps).
If you have 4A Power Supply then see what happend as in below exp:
Example 1: You have 2 domes drawing 1 Amp each and 6 cameras, drawing 150mA each. Your total current draw is 2.9 Amps, well within the total available current of 4 Amps. This is OK.
Example 2: You have 5 domes, drawing 1 Amp each and 3 cameras, drawing 150 mA each. Your total current draw is 5.45 Amps, exceeding the total available current of 4 Amps. This in not OK. Your installation will not work.
Practically Major Camera showing Video Loss due to use of multi camera power supply (8 in 1, 4 in 1, etc) in India. Maximum Indian (Mainly Stores, Hospital, Small Office, Hotels etc) used multi camera power supply due to low price (In 2012 you can get 12V@5A Power supply Rs. 1200/-). Where as Power Plant, Big Organization etc used 12V@1A power supply per camera (In 2012 you can get it Rs. 300.00/-) Just Imagine if you have more then 08 nos of camera.Also Visit: http://arindamcctvaccesscontrol.blogspot.in/2012/11/voltage-amperage-guide-for-your-cctv.html