Planning, design &
Erecting of
Video surveillance systems
Code of practice for Campus
1. Introduction
Decades worth of surveys have demonstrated that families and students place campus safety and security at the forefront of the decision-making process when deciding on where to enroll. The global market for school & campus security is anticipated to account for a substantial revenue generation of more than USD 2.54 billion by 2025, expanding at a considerable CAGR of 19.7% over the review period (2019-2024).
Keeping our nation’s college and university population safe and secure requires the partnership of college administrators, law enforcement and security professionals. Many campuses are ramping up their security to ensure their students, staff and visitors continue to remain safe and to protect their reputation as a secure school.
Children spend a large part of their day in schools and while travelling to and from their schools. “Right from the time when students enters a campus or school / university premises till the time they leave, the campus team is responsible for any kind of misshapen with them.” – This is not just a statement, but one of the biggest risks that all campus have.
Proper evidence is required to check out the facts which can be provided by CCTV footages. This is the reason why surveillance cameras are often installed in the premises of campus or school or college or university. The installation of CCTV equipment can be a one-off cost that acts as a powerful deterrent for opportunistic criminals.
The correct design and use of such systems is paramount to ensure a CCTV surveillance system meets the needs of the user, provides a tangible benefit and provides safety and security for the wider law-abiding public.
NOTE: In this context, the term Video Surveillance System (VSS) synonymous with CCTV.
2. Scope
This
code of practice gives recommendations for the planning, design of all Video
surveillance systems.
This code of practice has been prepared to assist in this process by taking account of the various standards for Video surveillance systems, and presenting them in a useable framework necessary to achieve an effective security surveillance solution.
3. Objectives & Planning
3.1 The
specific objectives which these guidelines aim to achieve is the Video
Surveillance security
of children at schools, specifically safety in each of the following aspects:
a. from
risk of kidnapping by any person, within or outside the school while at or
travelling to and from the school on school buses, or while on school trips.
b. from
abuse, be it verbal, physical or sexual by any member of staff, be it
teaching/non-teaching/contractual, older students or any other person while on
the premises or on the transport route.
c. from bullying, threats by older children (specific attention is drawn to problem as reported of older children seeking protection money or favours from younger children)
d. from
internet/cyberbullying/abuse on facebook/twitter/youtube etc., by circulation
of undesirable/objectionable material by school children or staff involving
school children
e. from
misuse of electronic/telephonic media at schools leading to obscene
emails/texts /videos/etc. during or after school hours by students or staff
involving school children
f. from
traffic accidents at/outside premises while boarding buses, crossing roads in
vicinity, etc.
g. from
accidents on premises due to fire/short circuits etc.
h. from any
accidents during travel on school buses or while on school trips
i. from threats by natural calamities such as earthquakes, flooding, etc. by adequate preparation to mitigate the disastrous impact of such events.
The above objectives help to determine the quality and level of security that you will need. Usually, campus with low-risk environments require basic surveillance security and those in danger zones have a high priority security system.
The main key component of video surveillance is Camera, Storage (NVR/DVR/NAS) & image Presentation Devices. Video analytics, ANPR etc are optional. There are two technology of Video Surveillance system, Analog & Digital/IP. Here are the different types Of CCTV Cameras: Dome Camera, Bullet / Box Camera, Zoom Camera, Speed Dome/PTZ Camera, Panoramic Camera.
3.2 Capturing user need
It is the responsibility of the system specifier or purchaser to identify and record the purpose of the video surveillance system. When planning CCTV systems it is important to remember that there is no ‘one size fits all’ solution. Each site will have its own unique needs based around numerous factors (including nature of site, geographic location, local environment, history of issues). Similarly each end user will likely have their own expectations regarding what the system will do for them (e.g. deter crime, improve detection of crime, monitoring movement of personnel).
If you are a Head Master / principal / owner / register, ensuring everything going right is definitely one of your major responsibilities. Toilet surveillance is illegal. CCTV security cameras in toilet are NOT allowed. Installing security cameras in bathrooms is a serious privacy violation. You can plan to install sensor just to get information latrine are used or vacant.
3.3 Risk assessment
Risk assessment should be performed to ensure the design of the
system results in an installation that adequately addresses the threats and
reduces the security risks. In order to identify the level(s) of security
required (and potentially therefore the grading of the elements of the system),
an assessment of the factors which are likely to come into play is required. In
very global terms, from a security perspective these elements are typically
considered as:
Threat (Who): The
threat will typically be defined as the persons or events to be protected
against. Threats will vary greatly in termsof objectives, determination,
capability, resourcefulness,
Vulnerability (What / Where): The vulnerability will typically be the areas of concern that
require protection. The level of vulnerability will be defined by numerous
factors such as desirability of the objects in the area, ease of access, campus
operational hours of the environment, exposure / secluded nature of the area.
Risk (What if?): Risk is effectively the consequence of a successful or
attempted intrusion or event. These risks can be wide and varied and not
immediately obvious. Risks and impact levels of each identified risk will
typically vary depending on the nature of site. Risks can include:
1.
Immediate Financial Loss:
Immediate value of items lost.
2.
Ongoing Financial Loss: Increased
insurance premiums, time to return to profit.
3.
Personal Safety: Injuries to teachers,
professors staff and / or members of public involved in violent incident.
4.
Stress Related Issues: Reduced
staff morale, loss of staff due to safety concerns.
5.
Non-financial loss: May include
loss of intellectual property, school / university data or similar.
Typically security systems cannot change the identified threat or alter the risk, but well deployed security measures significantly reduce the vulnerability. This in turn helps to reduce the likelihood of risks occurring.
3.4. Operational requirements and agreeing with the customer
Ideally the Operational requirements (OR) document should be raised by the end-user or their authorized representative (such as a security consultant) and used as the basis for specifying the required system and subsequent performance tests. Planned or possible future expansions to the system, including addition of further cameras, monitoring locations and integration with other systems.
3.5 Target Capture and Image Detail
Detection, Recognition and Identification
(DRI) in video surveillance is very important terms to get image details. DRI
ranges, expressed in meters, km (or miles), can be found in the specification
table of infrared camera brochures.
The
terms “Detection”, “Recognition” and “Identification” were defined as follow:
·
Detection: ability to distinguish an object
from the background
·
Recognition: ability to classify the object
class (animal, human, vehicle, …)
· Identification: ability to describe the object in details (a man with a hat, a Jeep …)
As a best practice, do not assume the camera resolution is everything in regards to image quality. For a camera to operate in a day-night environment, (the absence of light is zero lux), the night mode must be sensitive to the infrared spectrum. It is highly recommended to conduct tests or pilot installations before buying large quantities of any model of camera.
A
lens is a transparent optical device with perfect or approximate axial symmetry
which transmits and refracts light, converging or diverging the transmitted
light and to form images. A simple lens consists of a single optical element. A
compound lens is an array of simple lenses (elements) with a common axis; the
use of multiple elements allows more optical aberrations to be corrected than
is possible with a single element. Lenses are typically made of glass or
transparent plastic.
The practical effect of this is that a camera may need to have a wider or narrower field of view so that the necessary amount of detail can be seen and that in some circumstances more cameras may be needed, either to increase the area covered with the same detail or to allow for different levels of detail to be seen from the same view.
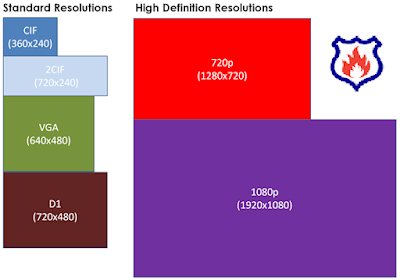
The measure of the fine detail that can be seen in an image. For analog systems this is typically measured in Television Lines or TVL. Higher TVL rating, the higher the resolution. Same way megapixel (MP) like 1.3mp, 2mp, 4mp, 8mp etc.
The graphic below shows a comparison of the resolutions listed if each pixel takes up the same amount of space.
Key camera
areas, include exterior entrances and exits, parking lots, the
front-desk area, the lift, the floor corridor, the Hostel lobby,
cooking area, linen room, bar, casino and swimming pool exterior area.
Account should also be made of the difference between live operation and playback / review operation when considering image size requirements. For example, in a live monitoring situation, where a rapid assessment of the scene or situation may be needed, a higher screen occupation may be required than a system which is required to be more ‘reactive’, whereby little or no live interaction is anticipated and recordings / events can be reviewed in slower time.
3.6 Environmental considerations
Consideration
should be given to the need for specialist equipment or installation techniques
in certain environments.
Consideration of environmental requirements should be given to areas which may not be immediately obvious. For example where hard disk storage systems are to be installed which may, in their own right, raise the local temperature to an extent whereby artificial cooling methods such as air conditioning are required to help ensure longevity of the equipment.
3.7 Regulations and Legal Requirements relevant to CCTV
There are many legal requirements and regulations that apply to CCTV including those listed here. It is the responsibility of the owner, installer, Maintenance Company and operator to ensure compliance with these as appropriate to their activities and location. Consideration should also be given to other byelaws introduced by local government. These will vary from region to region.
The
following Acts of Parliament are known to affect the majority of CCTV
installations and use of CCTV but others will apply in specific circumstances:
1.
The Human Rights Act 1993(Amendment Act,
2006)
2.
The Data Protection Act 1998 (DPA).
3.
The Right to Information Act 2005
4.
The Private Security Industry Act 2005
5. The Clean Environment Act
4.Design
4.1. Site Survey
A site (School, Collage, university, Hostel, Private study point… etc) survey should be conducted to take into account specifics of the site along with the OR. Locations of interest should be established and documented on the site plan ( if floor, each floor drawing). Accordingly select camera type, quality of picture etc. The site survey should consider lighting. Depending on circumstances day and night time surveys may be required.
The
performance of a CCTV system is primarily dependent upon the available light
level. It is important, therefore, that the limits of light levels within which
a CCTV installation is intended to function are expressed in units of
illumination (e.g. lux).
Light levels are normally measured in lux, the SI unit of luminance. In some cases the amount of light will be quoted in foot-candles. One foot candle is approximately ten lux. Lux levels apply only to visible light spectrum and are not relevant to infrared systems
Lux is measurement of the intensity of light. It is equal to the illumination of a surface one meter away from a single candle.
The survey should be used to decide the positioning of all key equipment of the system along with the necessary environmental protection requirements.
The site survey should consider power and device interconnection together with provision of local power supplies, routing of cables, wireless links, etc.
During the survey consideration should be given to how the equipment will be installed and other considerations such as accessibility, access times, need for closures whilst equipment is being installed and accessibility for maintenance.
Cameras
must cover all critical areas of the premises. Areas for specific attention are
as indicated:
1.
Entry and exit points of the school (in case there is a side entrance, this too
must have a CCTV camera).
2.
All corridors and staircases
3.
Library, infirmary, auditorium
4.
Inside elevators
5.
Canteen, sports rooms, Electronics Lab, Chemistry Lab, Computer labs
6.
Entrance to classrooms
7.
Entrance to toilets
8.
Sports fields, swimming pools
9.
Areas where buses assemble
10.
Entry and exit point of premises
11. Any point on the outer perimeter/wall which is vulnerable, and which could show footage of persons attempting to gain entry to the premises, especially covering persons outside the main entrance.
While CCTV at entrance to toilets is essential, it is not permitted to fit CCTVs inside toilets, to ensure that dignity is not compromised.
External motion detectors and LED illuminators are crucial components for a security system. By integrating these separate technologies with video surveillance cameras, the site will benefit from one powerful security solution with versatile advantages.
4.2 Equipment Selection
Equipment means Camera, Storage, software, Viewing monitor etc. Consideration should include environmental factors (e.g. efficient use of power, disposal of consumable items, and control of hazardous substances).
4.2.1 Camera and lens
A
camera and lens should be compatible and should be selected to cover the area
to be viewed, taking into account any person or object required to be
identified.
Selection of the correct lens type is as important as the camera selection. A poor lens performance can significantly detract from the overall performance of the system. For further information refer to BS EN 62676-4 clause 6.5.
All vehicles entering and leaving the premises should be caught on camera with at least a 50-metre range with a clear image of the vehicle number.
4.2.2 Automated License
Plate Recognition
ALPR systems utilize high-tech cameras with accompanying software to detect the license plate of a car. Some of these ALPR systems also utilize sophisticated data analytics, to help locate vehicles in question, or even identify a license plate number, when that vehicle has been used in connection with a past crime. These systems also have been used in a number of documented instances to locate missing children or kidnapped individuals by locating a subject vehicle. ALPR systems have also been used commercially as security measures to identify vehicles that do not belong at a particular location (unknown vehicle) or a vehicle that security officials have identified as a security risk (known vehicle).
ALPR systems can be reconfigured for use in a school security setting to assist school security officials to help identify a vehicle that does not belong on a campus or conversely, flag a vehicle that is restricted from being on school grounds. These camera systems would be deployed on the outer perimeter, typically on an access road either approaching or entering a school parking lot.
4.2.3 Sensitivity of Light
When selecting a camera for a particular application, consideration should be given to the type of light source and the spectral response of the imaging device in addition to the scene reflectance and lens. Available light level will have a major influence on the choice of camera and typically the sensitivity of a camera measured under laboratory conditions may not match results under natural operating environments. There may be a trade-off between higher resolution cameras and a reduction in sensitivities.
Wide dynamic range cameras can help compensate for large variations of luminance across a scene and provide acceptable exposures simultaneously in the brightest and darkest areas of the image.
4.2.4 Field view
The width and height or area desired to be covered by one camera. This area is determined by the focal length of the lens on the camera and the distance the camera is mounted from the scene. The equipment selection should ensure the field of view matches the system’s operational requirements.
4.2.5 Illumination
A video surveillance camera requires a certain amount of lights produced by natural or artificial illumination. The amount of lights is defined by LUX(Lumens per Square Meter). Depending on the choice of camera equipment and the system’s operational requirements extra illumination may be required.
Refer to BS EN 62676-4 clause 6.9 for points to consider e.g. positioning, beam pattern, maintenance, deterioration of light source with age, unwanted reflections, type of lighting and switching.
4.2.6 Housings and mountings
A camera and its supporting hardware should be securely mounted. The camera mounting bracket or pole should safely support the weight and wind age of the camera and of any associated hardware. Remember that a small amount of deflection in a pole when a camera is fully zoomed in at a distant target will result in large degrees of movement in the scene.
Consideration should be given to the environmental conditions in which the equipment is intended to operate with respect to the additional features which may be implemented into housings i.e. heaters, wipers.
Protection against malicious damage either though forceful impact, scratching or burning plastic windows or dome bubbles, or spraying should be addressed by using a combination of housing specification and physical positioning.
All equipment installed should be suitable to withstand the prevailing environmental conditions according to the environmental classes in BS EN 62676-1-1. This includes protection against dust, particles, water and any special environmental conditions that may prevail on the site (e.g. corrosive or explosive atmospheres).
4.2.7 PTZ Mechanisms
PTZ
indicate Pan, Tilt & Zoom, so a camera having this three feature is called
PTZ camera or speed Dome camera. Hostel Parking area, main gate entrance, open
out door space, swimming pool, playground, sea beach etc area should cover by
speed dome camera.
The maximum required pan and tilt rotation angles and any intermediate preset stops is required. IP66 based enclosure should protect out door speed dome camera.
4.2.8 Powering
Consideration
should be given to the power requirements of the system. This includes:
•
Local or centrally powered (Must be UPS power)
•
Mains or low voltage. (110V to 220V AC)
• Back up / Stand-by power in the event of mains failure.
For Power over Ethernet (PoE) consider the potential need for high power PoE supplies for certain cameras, especially ones with in-built illuminators, heaters or motorised PTZ functions. For PoE also consider the limiting distance factor of 90m in order to deliver the maximum power from the power sourcing equipment (PoE injector) to the powered device. Greater distances will adversely affect performance of the cabling including bandwidth.
The outdoor surveillance cameras record everything in real-time and this recording is stamped with date and time. This becomes a proof of evidence in determining whether the claims are genuine or fake. Sometimes, it happens that student get injured by their own mistakes, such as because of being drunk or careless attitude.
4.2.9 Video performance
Equipment and system design should take into account the need to achieve performance levels and characteristics as stated in the operational requirements. This should include consideration of frame rate, resolution and quality of live and recorded images both for human viewing and for automated video analytics.
In cases of injuries borne on the property, CCTV ascertains whether the injury was because of misbehavior of the guest, or an accident, or the negligence of the business organization itself. Suppose a drunk student was misbehaving with the decorations in the open area of the property and then they got injured. In such a case, they may blame the hostel authority and file a lawsuit against them. But if the hostel has CCTV recordings collected from the CCTV outdoor surveillance cameras, they can easily prove their innocence and huge compensation money can be saved this way.
There are some people who try to make some quick money by filing a fake lawsuit against hostel providers. Generally its done by female students. It is commonly known that most slip and fall cases happen near the pool area. Over there, some students may get injury by colliding with someone else and may complain that the injury was a result of the hostels negligence near the pool area. If outdoor surveillance cameras are installed in the premises, then by seeing the recording, the hostel authority can easily prove that the injury was nothing but a result of collision. But if there was no CCTV installed then a lawsuit could have swept away thousands or even millions from the hostel’s account.
4.2.10 LAN Switches and Provisioning
A
separate security network is recommended and should be different from the man
Operational network. This means that dedicated switches, routers and other
networking appliances should be used solely by the security systems. The reasons
for keeping the security network independent of the data network are as under:
·
Additional
security measures are required to protect the security network from internal
and external threats.
· The security network requires substantial amount of bandwidth and sharing of network with other users might pose challenges to sharing of bandwidth.
LAN
switching requirements are covered in the necessary detail for a successful
deployment. There are several requirements for LAN switches, the primary being
the ability to support the 802.1af PoE standard for those cameras that can make
use of this feature. Also, aggregate backplane capacity as well as uplink
capacity is important. At a minimum, switches should have 1Gigbps or 10Gigbps
uplink and a 32Gbps effective backplane capacity. QoS support is also
important, the ability to both trust the Layer-3 QoS markings (DSCP) and to set
DSCP on ingress is critical. Most of commercially available switches support
VLANs and trunking and these features are critical for segmenting IP video
surveillance traffic into its own domain.
Support of features like port security, 802.1x port-based Network Access Control (NAC), Spanning Tree Protocol (STP) Port Fast feature, and PortFast Bridge Protocol Data Unit (BPDU) guard are also useful. Because this design guide recommends marking video surveillance media streams as DSCP value CS5, switches that are configured by default for VoIP implementations are recommended as the media feeds will align with the default VoIP configurations.
4.2.11 IP Addressing Requirements
If
the network manager plans on implementing some segmentation and path isolation
over the LAN/WAN by using VRF-Lite and VLANS, the IP addressing scheme may have
greater flexibility than if the video surveillance networks are routed in the
global routing table. However, the general recommendations for addressing IP
video surveillance devices are as follows:
•![]() Allocate an addressing
scheme distinct from the end-user address space at the branch locations.
Allocate an addressing
scheme distinct from the end-user address space at the branch locations.
•![]() Allocate network addressing
so that IP cameras, servers, encoders, workstations, and any Hostel building
management (BM) devices can be allocated from the address space at the remote
locations.
Allocate network addressing
so that IP cameras, servers, encoders, workstations, and any Hostel building
management (BM) devices can be allocated from the address space at the remote
locations.
•![]() Allocate addressing to
facilitate summarization of network advertisements to the core.
Allocate addressing to
facilitate summarization of network advertisements to the core.
•![]() Allocate addressing so that
one network advertisement can encompass the entire address space for physical
security (and building management) devices.
Allocate addressing so that
one network advertisement can encompass the entire address space for physical
security (and building management) devices.
•![]() Configure a loopback
address on remote routers from the physical security address space for NTP and
other management functions.
Configure a loopback
address on remote routers from the physical security address space for NTP and
other management functions.
Because the IP cameras are using static IP addresses, give careful attention to IP addressing deployed as reallocating IP addressing is more time consuming than when all end nodes use dynamically assigned IP addresses from a DHCP server.
4.2.12 Storage
The total storage requirement for a digital CCTV recorder should be estimated before a system is installed, so that hard drives of the appropriate capacity can be specified. It is vital to ensure that sufficient capacity is available so that compromises do not have to be made on either the image quality or retention time.
The storage requirement will depend on factors such as whether just video, or video and audio are being stored, frame size, required number of frames per second, number of cameras, bit rate of video and audio streams, retention period, requirements for storage resilience (e.g. mirroring or RAID storage), and operating system overhead. Recording of video footage must be on 45days basis first in first out.
In
general, the recommendation is to store data as close to the source as
practical. This is especially true of branch location deployments. By storing
video archives locally, IP video surveillance may be deployed to locations with
traditional WAN links that would otherwise not have enough bandwidth to
transport the archives to a central campus/data center facility. The WAN,
however, may still have sufficient bandwidth to transport or view video clips
to aid in investigations or other forensic analysis. By storing locally and
only transporting the small amount of video surveillance data that is needed
centrally, video surveillance can be network-enabled today and tied into other
BMS and analytics solutions that can benefit the business.
When
using MJPEG streams, the frame size of each image plays a key role in
estimating the storage and transmission requirements. Since each frame is
unique and varies according to the image complexity, it is difficult to provide
a guide that provides fixed frame sizes. An IP camera that provides images with
low complexity will generate smaller frame sizes. Smaller frames will require
less bandwidth and storage capacity.
The following formula is used to calculate the bandwidth
requirements for MJPEG streams:
MJPEG storage = Average Frame size x Frame rate x duration
Example 1: For an 8-hour archive of a CIF
video stream with 50 percent quality and 15 frames per second, the following is
the calculation:
4 KB x
15fps x 3600s
= 216,000 KB/ hour
Example 2: For a 24-hour archive of a 4CIF video stream
with 100 percent quality and 5 frames per second, the following is the
calculation:
320 KB x 5fps x
3600s =
5,760,000 KB /hour
= 5,760MB /hour = 5.76GB /hour x 24 hours. = 138.24 GB
The
following formula is used to calculate the bandwidth requirements for MPEG-4
streams:
MPEG4 storage = Bit rate (kbps) x duration
The target bit rate is configured on the camera and is already expressed in bits per second.
The
following aspects cater for redundancy:
CCTV cabling – star topology.
Parallel recording or failover recording in at least n+1 mode.
Layer 3 switch – n:1 redundancy.
Fail over video management system license.
Storage – minimum RAID 5.
For scalability, the servers and switches should be loaded up to 80% only.
4.2.13 Image Presentation Devices
The image presentation device(s) should be selected after taking account of the nature of the image viewing task, the conditions in the control room or other viewing space and the need to identify, recognize, detect or monitor. It should be considered whether displays are also used for viewing maps, floor plans, device lists, system status, alarm conditions, etc. When displaying images where a significant amount of movement is present (e.g. traffic / Cab entry exit) display refresh rates and resolutions should be matched to the image source.
Display screens have different resolution depending on set-up and type. Display resolution should be selected to match and complement the camera resolution and resultant video resolution.
For larger display surfaces, the efficient display resolution can be defined according to the minimum visible size of a pixel. The size and resolution of display screens should be considered together with the recommended display sizes. An operator placed at a large distance may not be able to discern the details of a small high-resolution monitor.
CCTV cameras not only save businesses from lawsuits but also keep the guests tension-free at all times. The concerns of the guests regarding their expensive cars are automatically resolved when they see the parking area is monitored by outdoor surveillance cameras. Some businesses may not be too wealthy to appoint a security guard in every sensitive area of their premises, so going for CCTV cameras will be a good idea. It is a one-time investment that constraints the effort of opportunistic criminals.
4.3 Proposal Including System Design Site Plan
Once the site survey and Operational requirements (OR) is completed the CCTV system can be designed and a System Design Proposal (SDP) prepared.
Where an OR is not available, as may be the case for less complex CCTV systems, the SDP, drawn up as part of the process of ascertaining the customer’s needs, expectations, and patterns of usage of the premises, forms the basis of the agreement between the installing company and the customer as regards the CCTV system to be supplied. At appropriate stages checks should be made to ensure that the proposed implementation will meet the customers’ operational requirements. The operational requirement and matching test procedure is essential to assess whether the system can meet its required purpose.
The design should take into account the various requirement and location factors identified in the previous stages. At this stage a site plan should be drawn up, including locations for the various key components e.g. cameras (including field of view), and PTZ preset positions, detectors (including range and coverage), control rooms, power supplies, interconnections, etc.
The system design proposal should stipulate the conditions under which any test image(s) should be used. For example if the system will be used in both day and night conditions then separate tests should be performed for the different light conditions.
The site plan may be drawn on CAD, or be a hand drawn sketch with annotated pictures taken by a digital camera as appropriate
Any change to site plans, installation plans, system designs and/or logical architecture should be included and attached to the final documentation and it should include change permissions and risk/issue/logs generated during the installation process.
4.4 Video transmission
Video transmission describes the transfer of video from a capture device (camera) to a viewing device (or software), a recording device (or software) or to a storage device using switched networks. The networks may be hard wired or may be wireless. Networks may combine different methods of transmission, e.g. typically described as analogue or IP.
In the case of both wired and wireless networks, sufficient defences should be put in place in order to protect the end user to ensure that the video transmission system is not vulnerable to attack from outside potentially rendering the asset unprotected, or used as a means of penetrating another network to obtain otherwise confidential information.
The use of IP technology is becoming more widespread across a variety of applications and industries. The security industry is no exception. IP can often be used to provide a cost-effective means of installing/monitoring security systems by exploiting existing infrastructure and enhancing and/or replacing older arrangements.
If an Alarm Receiving Centre (ARC) wishes to provide remote monitoring & remote viewing of IP enabled systems, they will have to design and implement robust network solutions.
A network can be built up from many differing types of service. One of the more common is ADSL (Broadband) but there is also SDSL, leased lines, megastreams, kilostreams, GPRS (Cellular network), ISDN Dialup, PSTN Dialup and quite a few other options in the form of direct links to service providers.
4.5 Bandwidth requirements
While one single alarm system uses very small amounts of bandwidth, monitoring several hundred or even thousands could have a dramatic impact on the ARC links, i.e. consider open/close signals happening at more or less the same time every day from all systems.
It is unlikely that all these signals would be sent at exactly the same time so bandwidth is unlikely to be of major concern to the ARC for a small number of systems. However, as you start to calculate bandwidth requirements for CCTV you can see that you quickly begin to use up the available bandwidth.
For alarms, you should be more concerned with hardware systems able to process a high number of systems simultaneously. e.g, firewalls, receivers/servers.
However, a CCTV system sending multiple data streams could require significant bandwidth in much the same way as a DoS attack (Denial of Service). There should be systems in place to address these concerns.
There
are various benefits of installing CCTV cameras in Hostel premises. Some of
them are discussed below:
- Beside rooms, there
are various facilities that Hostels provide such as gym, swimming pool
etc. Presence of CCTV at these places helps to identify intruders and
management can take quick action to restrict them from entering the place.
- CCTV cameras help curb
unwanted access like that of intruders and uncategorized customers to Hostel
facilities like pool or Gym etc.
- The presence of CCTV
cameras in Hostel parking, corridors and entrances give a sense of
security to the parents. This has become a major selling point in Hostels
today.
- 24/7 surveillance
facilities of entry and exit areas help restrict trespassers from entering
the premises.
- CCTV when installed in
storage or maintenance rooms of Hostels helps in preventing a possible
theft by employees. Employees also hesitate to do any unethical activities
when they see a CCTV camera is installed and realizes
they are being monitored.
- Presence of CCTV
cameras in Hostel’s building and especially in parking area gives mental
peace and satisfaction to parents.
- There are some
unexpected activities such as slips, falls or fights that happen with students.
In such cases, the customer files a lawsuit against the Hostel and demands
alimony. To bring the truth out, management should analyse CCTV recording
and if they find that it happened because of negligence of Hostel, they
should quickly resolve the matter with client. If they see that Hostel is
not responsible for whatever happened, they can counter the allegation and
can use CCTV footage as evidence.
- These footage play a
key role in evading fraud lawsuits against the Hostel and gather evidence
in investigations. In case of in-house charges, CCTV camera footage helps
prove Hostel claim or accusations against students and in case of criminal
investigations help the police gather evidence.
- There are some students
who harm the property such as damaging furniture in common area or the
decorations and when they are fined, they deny. In such cases, CCTV
footage acts as evidence and strengthens the Hostel’s viewpoint.
When
CCTV cameras are installed in your Hostel premise, you and your parents can
remain tension free and focus on the event. While installing the cameras, the
management should consider that the cameras does not invade the privacy of any
manner, the only purpose of installing the cameras should be safety and
security of the students and Hostel premise.
5. Installation
5.1 Evaluation of Equipment
Where a customization of a product/software is undertaken in order to meet specific user needs, the customization should be tested equipment before being deployed. The customization should also be tested against the user need defined. Equipment may be required to exchange information in order to perform a function of some kind (for example, to move a PTZ camera to a position based on an input from another system, or increase the record rate and resolution of a device based on the inputs from another device). In these cases it is recommended the successful operation of the devices be tested first before being deployed. This is particularly recommended if the equipment is made by different manufacturers.
5.2 Cable laying
Security
camera cable is an important part of CCTV industry. The requirements of BS
7671 (Requirements for electrical installations, IET Wiring Regulations) should
be met using the edition current at the time of installation.
All interconnecting cables should be fixed and supported and installed to conform to good working practices.
As we all know wired CCTV camera footage totally depend on the wiring system. If cabling exposed, then it can be get tempered and you cannot get a video for a crime evidence. Each and every cable of the camera never revealed, especially for the outdoor environment. Covering all camera cable, also reduce the service issues.
Possible
fixings and supports include:
•
Conduit: when metal (MS) is used, suitable bushes or grommets should be fixed
to each end to prevent damage to the cable. When conduit is used to carry the
cable it should terminate as close as possible to the unit to be connected.
•
PVC or metal trunking: where trunking is used to carry the cable it should
terminate as close as possible to the unit to be connected.
•
Insulated clips
•
Cable ties
• Catenary Cables: When overhead catenary wires with loop holders or plastic buckles are used the supporting wire should be securely attached to the building. Self-supporting catenary cables may be used provided they are correctly designed.
Camera cable is basically manufactured in such a way that it should optimize video signal quality. CCTV camera cable is composed of two sub cables that will run simultaneously for transmitting both video and power signal, Analog Video transmitting cable also called RJ59 Cable, one sub cable is the central solid copper conductor core shielded by dielectric material, then further shielded by copper or alloy braid that will transmit video signal and another is power cables that will transmit power and both two-part is insulated by PVC having diameter of 5.5 mm to 7.5 mm. IP Video transmitting cable called CAT6 / CAT 6A etc.
All
cables should be of a type and size appropriate to the application and should
take account of transmission rate, electrical interference and voltage drop.
Any plastic or PVC component used as part of the installation of cables should be suitable for the environment in which it is installed. Externally mounted ties and clips should be made of UV-resistant material.
Environmental conditions such as dampness, excessive heat, risk of corrosion, mechanical or chemical damage, should be taken into account when determining the degree of protection required for cable runs.
Any cables used underground should be suitable for that purpose and have adequate protection from mechanical damage. Underground cables should provide a high level of resistance to dampness, chemical reactions, corrosion and rodents.
5.3 Power Supplies Equipment
Power supplies should be capable of meeting the largest load likely to be placed upon them under normal operating conditions. The maximum load on the power supply typically occurs during start-up of the system following a power failure. The assessment of the electrical current demands for design purposes should also include an extra tolerance of 5% to 10% over capacity.
Where safety and security considerations do not require continued operation of the CCTV system during a mains supply failure, the public mains supply may be the sole supply for the system.
Power
supplies should be located within a secure area, in a position safe from
tampering, and should be ventilated in accordance with manufacturers’
requirements for safe operation.
All equipment housings should be clearly marked with the operating, or supplied, voltage, whichever is higher.
The installation and position of additional power supplies should be considered if voltage drop across cables is likely to reduce the voltage to equipment to an unacceptable level. Alternatively, in some cases, it may be possible to reduce the voltage drop in the cables by using cables with less resistance, greater conductor size or by using more cores of a cable for the supply of power.
5.4 Camera Equipment
In
CCTV installation, the position of the camera plays a major role. if
you want to record a good footage from CCTV camera then you need find a best
place for it. Cameras should be mounted in positions free from obstructions and,
wherever possible, not directly viewing bright light sources. The mounting
position should allow installation and maintenance to be carried out in a safe
manner.
If
cameras are to be mounted on towers or brackets the following environmental
considerations should be made:
·
Rigidity,
taking into account potential wind velocity, equipment type and equipment
mounting and fixing positions.
·
Electrical
interference and the possibility of damage by lightning (see BS EN 62305).
·
Dust,
airborne particles and other potential sources of corrosion or contamination.
·
Condensation
inside housings and other equipment due to changing temperatures.
Tower and bracket equipment should be installed according to the manufacturer’s instructions and within loading specifications.
Where
movement of towers is possible, cables and cameras should be installed with
their safety and protection against tampering taken into consideration.
The alignment and mounting of line of sight transmission equipment (e.g. optical and microwave) is often critical and consideration should be given to the method of alignment and to the rigidity of the mounting.
Wired connections should, wherever possible, be concealed. Mechanical protection of flexible cable to movable cameras should be considered where physical damage is a possibility e.g. metal conduit or flexible conduit.
The camera should be installed in such a way that it is difficult for an unauthorised person to change the field of view of the camera. This can be achieved by installing at a suitable location and height, the use of appropriate physical mounting and possibly further by the use of security fixings.
Consideration should be given to the detection of loss of video signal, camera obscuring or blinding on any connected camera. An audible and/or visual system alarm should be generated to inform system operators that acknowledgement is needed and, if defined in the OR, this alarm should be mapped to an output for connection to an alarm system.
5.5 Recording Equipment
The environmental conditions under which equipment will be expected to operate should be taken into account and environmental housings affording appropriate protection should be specified.
Equipment should be installed to manufacturers’ instructions. To reduce the risk of condensation a heater should be installed within housings that may be subject to changes in temperature.
Where there exists the possibility of penetration by solid objects, dust or water, housings that afford appropriate environmental protection should be used. This is typically quoted as an IP Rating. To prevent tampering, lockable enclosures should be considered to house the control and recording equipment. A method of user name and password to access control functions should be considered to restrict access to authorized operators.
For
all control and recording equipment the following should be taken into
consideration:-
a.
Temperature.
b.
Airflow of equipment (front to
back, side to side, bottom to top, etc), ensuring that the layout of equipment
does not have these intakes/outlets blocked.
c.
Humidity.
d.
Dust and other air
contamination.
e.
Vibration.
f.
Electrical interference.
g.
Rigidity, taking into account
high wind velocity.
h.
Ease of access for maintenance
and service.
i.
Convenience of operator use.
5.5 Display Screens
Display screens may be desk or wall mounted with consideration given to the ergonomics of the operator or principal. The display screens should be installed to minimise the effect of lighting, particularly sunlight, which can adversely affect the viewing experience. Wall or ceiling mounted display screens should be mounted using suitable brackets in accordance with manufacturer’s instructions.
Consideration should be given to the positioning of such screens to ensure they are above head height or not in a position where people may bang their head on them.
Dos and don’ts of CCTV installation
The do’s in this section are your
go-to suggestions for the maximum utilization and best establishment of your
CCTV network.
1.
Place
at least two cameras at the entrance and exit gate. So, that you can get a
clear view of the people entering and exiting the Hostel.
2.
Install
cameras in all open areas of the campus or hostel which is accessible like the pool, park, lobby, service corridor,
loading dock, service exit, and stairs. Stairs and service exit are most
commonly left out of the surveillance system as they are considered place less
visited or used by the student. But this is where most systems fail as in most
cases these become grounds for suspicious activities.
3.
CCTV
cameras are important in rooms which store safe deposit boxes, money or
sensitive information as these are the places which have the most chances of
theft. Though not regularly followed, it is advised to have hidden cameras in
these locations because in most cases criminals find a way to avoid detection
once they know where the camera is installed.
4. CCTV security network should be developed all around the campus or university from every angle to protect the campus or university from the neighborhood and unauthorized access.
Don’ts of CCTV installation: The
Don’ts majorly focuses on measures to prevent infringement of privacy. In
this network of CCTV cameras and cyber-security, privacy has become a major
concern.
1.
According
to the campus security and camera law, bathroom surveillance is illegal. So,
avoid installing cameras in bathrooms, you can install them in corridors so
that you know who went into the bathroom and when.
2.
Don’t
be swayed by the sales pitch, always opt for security systems which use
Category 5 or Category 6 twisted pair cables. Outdated tech is prone to
hacking, so it’s advised to have the latest.
3.
Don’t
waste your budget on Pan Tilt Zoom cameras, hoping to cover a large area with
zoom. It is not true nor is it efficient.
4.
Don’t
mount all your cameras on your on the ceiling or 15 feet walls. The height of
the camera prevents you from getting a good look at faces.
5. Avoid installing cameras in angles which could capture images inside a bathhouse, washroom on the campus or Hostel premises.
There are a lot of do’s and don’ts to Hostel security but this will give you a basic lay of the land Technology is moving leaps and bounds every year and it’s important to keep your system updated to beat the competition.
6. Commissioning, Handover and Documentation
Very important part once installation or erecting activity has completed. Maximum System integrator or vendors not mansion any commissioning handover cost on their BOQ. That way vendor run away and system remain un-commissioned.
Commissioning should consist of the inspection and testing of the installed system by the installation technician/engineers; handover requires the demonstration of the system to the user and the subsequent acceptance of the installation by the customer along with proper manual / handing over document.
6.1 Testing & Commissioning
A CCTV system test plan should be agreed and the tests should be selected to demonstrate during handover that the CCTV system meets the agreed specifications.
This
should include testing of the following aspects of the system(s):
•
All wiring is correctly terminated.
•
Supply voltage is correct to all appropriate parts of system. Where extra low
voltage cameras are used, the voltage at each camera should be recorded.
•
Operation of all monitoring, switching and recording equipment (including time
synchronisation) is satisfactory, including playback equipment.
•
Interfaces with alarms (e.g. movement alarms, fences) are satisfactory and
triggering of alarms is correct.
•
Beam interruption detectors are aligned correctly, where used for triggering
the CCTV system.
•
Appropriate notices to indicate CCTV in operation have been provided.
•
All indicator lamps are working.
• If a standby power supply is specified, ensuring that the system continues to operate correctly to specification when the mains supply is disconnected.
This
should also include testing of the following aspects for each camera:
•
Camera type and lens fitted is correct for each position.
•
Operation of all automatic and / or remotely controlled camera functions (e.g.
pan, tilt, zoom, focus, electronic iris and wiper) is satisfactory.
•
Correct setting of all pan and / or tilt limits.
•
Camera movement, and field(s) of view seen through the appropriate monitor(s),
is correct and free from obstruction.
•
Operation of electronic irises and focus is satisfactory under the range of
intended light levels (night conditions may be simulated through use of
suitable neutral density filters).
•
Satisfactory operation of supplementary lighting.
• Warning labels are in place in respect of possible sudden movement of camera positioning equipment and in respect of any devices that could cause injury, including damage to the eye.
There
are test methods given in:
BS
EN 50132-7:2012, Annex B or C
BS
EN 62676-4, Annex B or C
These test methods may be used wherever an objective evaluation is required to confirm that the required performance can be obtained. The use of the test methods listed above is a matter for agreement between customer and installer and is not a requirement for every installation. Other test methods are permissible.
Commissioning
should include visual and functional testing to ensure that:
a)
The system is installed in strict accordance with the agreed specification and
that the standard of workmanship is high, and
b) The commissioning requirements of this Code of Practice and BS EN 62676-4 or EN 50132-7 are met.
6.2 Handover
At
handover, the installing company should:
•
Demonstrate all aspects of the system operation to the customer, including any
necessary safety precautions.
•
Ensure that the correct documentation (see 6.3) is given to the customer to
enable the system to be operated, adjusted and maintained.
•
Train the system user(s) in its correct operation and arrange for any necessary
future training.
• Ensure that users know the procedure for summoning assistance in the event of system malfunction.
Following handover the customer should be asked to sign an acceptance document and to enter any confidential information (e.g. passwords which restrict user access to engineer and other reserved functions) required to make the system perform to the agreed specification.
Access to CCTV recorded images needs to be restricted and tightly controlled for Data Protection Act purposes. This means staff should only have access if they need it to achieve the purpose of the scheme. Third party access should be limited to law enforcement, prosecution agencies, legal representatives, the media (when assisting to catch a criminal) and people whose image has been recorded (unless it would prejudice criminal proceedings). All requests and reasons for denial need to be documented.
If individuals want to view recorded images of them, they need to apply to the data controller in writing and pay a small fee (max Rs50). The data controller must deal with the request within 30 days – even if it is to deny their application.
6.3 Documentation
Upon
completion of a CCTV installation there should be a record for each system
making up the installation, which should include the following information
where appropriate:
a)
The name and address of the protected site.
b)
The name and address of the customer.
c)
The location of each control unit and the type and location of each camera and
its associated hardware.
d)
An indication of the camera view(s), their purpose(s), and the area(s)
protected should be documented. The camera view(s) may be provided in the form
of a drawing, a hard copy printout or a video recording.
e)
The type and location of power supplies.
f)
Details of those cameras that the customer has the facility to manoeuvre or
isolate.
g)
The type and location of monitors and indicating and / or warning devices.
h)
Manufacturer’s documentation relating to equipment and its operational
settings/controls.
i)
Full instructions for the correct use of system including all type master &
operation passwords, including details of routine testing procedures and any
necessary maintenance requirements (see 7); possible sources of interference with
the system and equipment with which the system itself will interfere should be
identified.
j) The operation, storage and cycling of recording media.
The
make and model number of all items of equipment should be stated in the system
record. The system record (i.e. for the “as installed” system) should be agreed
with the customer and a copy provided to the customer.
The customer should be offered drawing(s) of the CCTV installation. Where symbols are used in drawings, a key to these symbols should always be provided to enable customers to understand the content of the drawings.
The customer should be provided with the record of the results of the objective test where this was agreed to be a requirement.
All documentation referring to a security system should be kept in a place to which access is restricted to authorized persons.
6.4 CCTV Signs
Students needs
to be aware that they are entering campus or hostel area that is being
monitored by CCTV surveillance equipment & operator review the video
footage. Signs should be placed so that they are clearly visible and legible.
The size of the sign will vary according to the circumstances of its location.
7.0 Maintenance
Effective and regular maintenance of a CCTV surveillance system is essential to ensure that the system remains reliable at all times. Regular maintenance by a service company, and effective failure reporting by the user, will enable potential problems to be identified at an early stage so that appropriate action can be taken. If you are end user, it’s your responsibility to select your service provider or service vendor. Basically who did the project that vendor win service maintenance contract. If earlier installer not responds then you move with new eligible service provider. Eligible means service provider should member of ASIS Int, FSAI India or ISHRAE, should have letter of appreciation from customer on CCTV, Fire Detection systems.
A
maintenance agreement should be agreed between the service company and the user
of the CCTV system and should include the following:
•
Preventative maintenance visits - Planned servicing of a system, carried out on
a scheduled basis.
•
Corrective maintenance - Emergency servicing of a system, or part thereof,
carried out in response to the development of a fault.
• User maintenance - Basic responsibility of the user to maintain operation of the CCTV system.
8.0 Monitoring
Monitoring requirements of a CCTV system will vary greatly dependent on many factors, such as whether there is a need to view live and / or recoded images, whether the monitoring be done locally and / or remotely, the complexity of the CCTV system and the type of response required be it a guarding, key-holder or perhaps police response.
For
the data that you receive from CCTV surveillance cameras to be of any use, the
images produced need to be as clear as possible. Viewing of live images on monitors
in the school are usually restricted to the operator and any other authorized person
where it is necessary for them to see it. The monitor has been positioned so
that it is only visible to staff and members of the public are not allowed
access to the area where staff can view them.
Recorded images are also viewed in a restricted area, such as a designated secure office. The monitoring or viewing of images from areas where an individual would have an expectation of privacy are restricted to authorized personnel.
For school, the control room is located in the Head teacher’s office as cameras show images that could not be seen by the public from the main reception and access to the CCTV control room is strictly limited to the Senior Leadership Team. The Head teacher will check and confirm the efficiency of the system daily and in particular that the equipment is properly recording and that cameras are functional.
8.1 Control Room
Attention should be given to the ambient lighting within the control room and, if the room has windows, how sunlight will affect the operators’ ability to monitor the system. This may influence the overall control room layout or require additional window blinds.
If the CCTV system has a requirement for live viewing, camera control, system management, or any other human intensive tasks, a control room should be specified to house these functions. The ‘control room’ could be a single workstation, or a large operations center.
The
operator should be presented with a manageable number of CCTV feeds (e.g. is
the operator able to suitably view 8 cameras and perform the viewing tasks
related to all of those camera views, and their anticipated levels of
activity?).
The camera view should be presented to the operator at a size sufficient to allow them to undertake the viewing tasks as above either routinely or by manual or automatic switching of views. (E.g. is the operator being presented with views intended for identification tasks, but displayed as part of a quad view, at a lower resolution, reducing the amount of information available to the operator?).
Spot displays should be positioned directly in front of the operator at between approximately 0.5 – 1.5m and of a sufficient size. They should also be placed so that the operator can easily turn their sitting position to face the displays.
8.2 Incident Response
Locally
agreed procedures should detail the action to be taken in the event of an
incident. These procedures should conform to those laid out as below:
•
Action to be taken
•
Who should respond?
•
The timescale for response
•
The times at which observation should take place
•
The criteria for a successful response
•CCTV operators should maintain a record of all incidents in the appropriate incident log.
The
overall indicator of successful response to incidents is that the CCTV scheme
fulfils its objectives, i.e.:
•
Restoration of tranquility
•
Dispersal or control of the situation
•
Prevention or minimization of injury and damage
•
Reduction of crime and disorder, to improve safety and reassure the guest
•
Identification of a suspect
•
Gathering relevant information to assist in the subsequent apprehension of
offenders
•
Apprehension of a suspect with evidence
•
Guest safety through effective evacuation
• Traffic flow restored
8.3 Recording quality and storage
No more images and information should be stored than that which is strictly required for the stated purpose of a surveillance camera system, and such images and information should be deleted once its purpose has been discharged.
Recorded material should be suitable for evidential use as required by the courts if it is to be admitted as evidence; it is therefore essential that recorded material evidence maintains total integrity and continuity at all times. Appropriate security measures should be taken to prevent unauthorized access to, or alteration, disclosure, destruction, accidental loss or destruction of recorded material.
Data should not be released to campus or hostel outside the ownership of the CCTV scheme, other than under guidelines referring to the release of information for the purposes of identifying alleged offenders or witnesses, in accordance with the particular CCTV control room’s policy and procedure.
8.4 Media use, storage and disposal
Recorded material should be stored in a secure environment, so that the integrity of the media is maintained. This includes recorded material that has been requested by the law enforcement agencies or contains a known incident. Controlled access to the recorded material storage area should be strictly maintained. Data that is to be destroyed should be destroyed under controlled operation. The register should show the life of the media at all stages whilst in the owner’s possession; such a register may also show itself to be useful in enabling evaluation of the CCTV scheme.
The
register should include the following:
•
Unique equipment reference number.
•
Time/date/person removing equipment from secure storage for use.
•
Time/date/person returning equipment to secure storage after use.
•
Remarks column to cover additional points (e.g. erase/destroy/handed over to
law enforcement agencies/removed from recording machine).
•
Time and date of delivery to the law enforcement agencies, identifying the law
enforcement agency officer concerned.
• In the event of a non-automated system of erasure of data, the time/date/person responsible for erasure and/or destruction.
8.5 Exporting recordings
When
exporting recordings the following procedure should be followed:
•
Maintain records of the operator(s) of the equipment. This enables the manager
to establish who was operating the equipment at any given time.
• Record without interruption, wherever practicable. Any interruption should be logged.
8.6 Optional Workstation
Of course, you can always turn your optional computer into a storage unit by configuring storage path to your computer; however, massive data storage could slow your computer down and eat up storage space rapidly.
Not only that, CCTV forage auditing you can do from computer. You need window license based software only. That software takes screenshot of your open Camera Viewing window. In this scenario you can see what camera saw. Camera see 24Hr, you are able to see within 24min, I am confirm your DVR / NVR can’t do it. ‘Auditing’ means 'seeing' what the cameras 'saw'. CCTV video footage should be audited daily; several times a day if need be. Depending on the requirements, auditing of CCTV footage of critical cameras on a daily basis must become an SOP. Auditing will help relevant stakeholders to ‘discover’ the 'unknown'. Auditing as an activity may be manual, it may be post-facto, but it is a very dedicated and systematic process, which helps address some of the challenges of live monitoring (video blindness, poor attention span, boredom, bias, fatigue etc.), as well as the challenges related to alert-based systems (how often has one faced false alerts, or what is called the ‘cry-wolf’ effect). Auditing will help discover issues as mentioned above as well as in identifying and analysing threats and hazards (THIRA/HIRA) of various kinds. Auditing CCTV video footage will also be extremely helpful in waste reduction and following the 5S philosophy, i.e. sort, set, shine, standardize and sustain (all part of Six Sigma practices). Moreover, in case of an accident/incident, relevant authorities can analyse CCTV video footage to determine whether implementing or improving existing policies, procedures, and processes could help reduce the potential for future occurrences.
And you can transfer those recordings from your computer to hard drive, pen drive, USB and etc accordingly.
9. Additional Information
School buses must mandatorily have GPS and CCTV cameras.
The School Bus-in-charge must ensure that the bus is being driven only by the authorized driver at all times on the route (especially in view of past accidents where some other underage/unlicensed driver has taken the wheel without being unauthorized to do so) by ascertaining from time to time with the teacher/didi on the bus, and/or viewing of bus CCTV footage.
Special care will be taken to ensure proper sealing and monitoring of areas which are unoccupied or used less often. Ideally, these should be covered by CCTV and the Vigilance officer must take a round of such areas every now and then to ensure safety is not compromised.
References·
BS EN 62676-4:2015 - Video surveillance
systems for use in security applications.
·
BS EN 11064-7:2006 - Ergonomic design of
control centres.
·
ANSI/BICSI 005-2016 – Electronic safety and
security system design and implementation best practices.
·
European Network and Information Security
Agency – Enabling and managing end to end resilience.
·
IPVM cabling best practices guide, Jan 3,
2018.