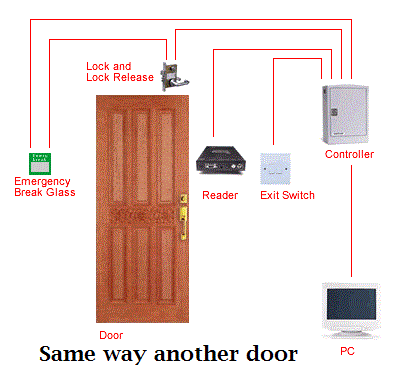
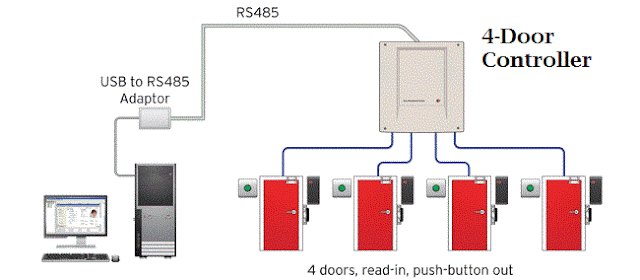
Globally Tailgating
is common problem
One of
the biggest weaknesses of automated access control systems is the fact that
most systems cannot actually control how many people enter the building when an
access card is presented. Most systems allow you to control which card works at
which door, but once an employee opens the door, any number of people can
follow behind the employee and enter into the building. Similarly, when an
employee exits the building, it is very easy for a person to grab the door and enter
the building as the employee is leaving.
This
practice is known as "tailgating" or "piggybacking".
Tailgating can be done overtly, where the intruder makes his presence known to
the employee. In many cases, the overt "tailgater" may even call out
to the employee to hold the door open for him or her. In these cases, good
etiquette usually wins out over good security practices, and the intruder is
willingly let into the building by the employee.
Tailgating
can also be done covertly, where the intruder waits near the outside of the
door and quickly enters once the employee leaves the area. This technique is
used most commonly during weekends and at nights, where the actions of the more
overt tailgater would be suspicious.
Solutions
To The "Tailgating" Problem
First,
recognize that the tailgating problem is probably the biggest weakness in your
security system. This is particularly true at doors that handle a high volume
of employee and visitor traffic. Many security managers spent a lot of time worrying
about unauthorized duplication of access cards and computer "hackers"
getting into their security system over the network. It is far more likely that
someone who wants access to your facility will simply "tailgate" into
the building rather than using one of these more exotic methods to breech your
security.
The
practice of overt tailgating can be reduced somewhat through employee security
awareness training. If employees are frequently reminded of the tailgating
problem, they are less likely to let a person that they do not know into the
building deliberately.
It is
difficult to overcome the problem of covert tailgating through employee
security awareness alone. While it would be possible to ask employees to wait
at the door until it locks after they pass, it is probably not likely that this
procedure would be followed except under the most extreme circumstances.
You can
follow this link http://arindamcctvaccesscontrol.blogspot.com/2015/11/anti-passback-in-access-control-systems.html "Regular
access control is more than adequate for standard control at entry points. Use
anti-tailgating systems to address a specific problem that could or has
happened" says Arindam Bhadra.
The
problem of covert tailgating can usually only be reliably solved through the
use of special "anti-tailgating" devices.
"Anti-Tailgating"
Devices
To
minimize the problem of tailgating, the security industry has created a number
of "anti-tailgating" devices. These devices include mechanical and
optical turnstiles, security revolving doors, security portals, and doorway
anti-tailgating devices.
The
essential function of each of these devices is that they permit only one person
to enter or leave the building at a time. They either do this by providing a
physical barrier that only allows one person to pass, or electronically by
providing sensors that detect when a person attempts to tailgate in, or when
more than one person tries to enter using the same card.
HALF-HEIGHT
MECHANICAL TURNSTILE
Description:
Rotating mechanical barrier arms installed at waist height prevent passage
through opening. Electrically-controlled, using valid access card causes arms
to unlock allowing passage of one person. Turnstile can be controlled in both
directions, or allow free-passage in one direction.
Approximate
cost: ₹ 4, 50,000 to ₹ 5, 50,000 per opening.
PROS:
Lowest cost anti-tailgating device, readily accepted by most users, relatively
unobtrusive, well-proven and reliable.
CONS: Can
easily be climbed over or under, requires separate door or gate for emergency
exit and for handicapped users, easily defeated by knowledgeable intruder, can
be somewhat noisy when operated.
Comments:
Good choice for use at visitor lobbies or employee entrances where cost is a
consideration. Works best when turnstile can be observed by security officer or
receptionist to allow detection of people climbing over or under the device.
FULL-HEIGHT
MECHANICAL TURNSTILE
Description:
Rotating mechanical barrier arms installed to prevent passage through opening.
Extends from floor to height of approximately eight feet.
Electrically-controlled, using valid access card causes arms to unlock allowing
passage of one person. Turnstile can be controlled in both directions, or allow
free-passage in one direction.
Approximate
cost: ₹ 14,50,000 to ₹ 15,50,000 per opening.
PROS:
Provides good security at a moderate cost. Well-proven and reliable.
CONS:
Obtrusive in appearance, requires separate door or gate for emergency exit and
for handicapped users, lacks sophisticated anti-piggybacking detection
features, can be somewhat noisy when operated.
Comments:
Good choice for commercial and industrial facilities where security and cost
considerations are more important than appearance.
OPTICAL
TURNSTILE
Description:
Consists of two freestanding pillars mounted on each side of opening. Equipped
with electronic sensor beams that transmit between pillars. Passing though
opening interrupts sensor beam and causes alarm unless valid access card has
first been used. Sensor beams are connected to computer processor that detects
when more than one person attempts to pass though opening on a single card.
Turnstile can be controlled in both directions, or allow free-passage in one
direction. Available with or without mechanical barrier arms and in a wide
variety of styles and finishes.
Approximate
cost: ₹ 20, 50,000 to ₹ 25, 50,000 per opening.
PROS:
Aesthetically-pleasing appearance, accommodates handicapped users, does not
require separate emergency exit, has sophisticated anti-piggybacking detection
systems, provides good visual and audible cues to users.
CONS:
Expensive, units without barrier arms provide no physical deterrent, must be
used at an entrance manned by security guard, relatively high "false
alarm" rate, some user training required to work effectively.
Comments:
Good choice for use in manned building lobbies where aesthetics prevent the use
of a half-height manual turnstile.
SECURITY
REVOLVING DOOR
Description:
Standard revolving door that has been specially modified for security use.
Extends from floor to a height of approximately eight feet. Typically has
multiple quadrants equipped with electronic sensors that detect number of
people in each quadrant. Use of valid access card allows one person to pass
through door, if more than one person attempts to enter, door sounds alarm and
reverses to prevent entry. Door can be controlled in one or both directions.
Approximate
cost: ₹ 70,00,000 to ₹ 75,00,000 per opening.
PROS:
Provides best protection against tailgating and piggybacking, fast, handles
high volumes of traffic, unobtrusive in appearance, provides energy savings
when used at exterior entrances.
CONS:
Very expensive, requires separate door or gate for emergency exit and for
handicapped users, door cannot be used for loading/unloading of large objects,
relatively high maintenance costs.
Comments:
Good choice for use at unattended building entrances where appearance is
important.
SECURITY
PORTAL (also called "Security Vestibule" or "Mantrap")
Description:
Consists of passageway with door at each end. Regular swinging doors or
automatic sliding doors can be used. Passageway is equipped with sensors that
detect total number of people present. Sensors can include electronic beams,
floor mat switches, and weight detectors. Video cameras with analytic software
can also be used (see video analytics below). To use, user enters passageway
and closes door behind him. He then proceeds to second door, and uses access
card to enter. If more than one person is present in passageway, portal sounds
an alarm and prevents entry. Portal can be controlled in one or both
directions.
Approximate
cost: ₹ 18,50,000 to ₹ 21,50,000 per opening.
PROS:
Provides good protection against tailgating and piggybacking, unobtrusive in
appearance, accommodates handicapped users, does not require separate emergency
exit, allows load/unloading of large objects.
CONS:
Expensive, relatively slow, cannot support large volumes of traffic, some
versions can have high maintenance costs.
Comments:
Good choice for use at unattended building entrances with relatively low
traffic volumes and for entrances into high security internal areas, such as
computer rooms.
DOORWAY
ANTI-TAILGATING DEVICE
Description:
Consists of devices installed on each side of regular doorway. Equipped with
electronic sensor beams that transmit between devices. Passing though opening
interrupts sensor beam and causes alarm unless valid access card has first been
used. Sensor beams are connected to computer processor that detects when more
than one person attempts to pass though opening on a single card. Doorway can
be controlled in both directions, or allow free-passage in one direction.
Approximate
cost: ₹ 6,00,000 to ₹ 7,00,000 per opening.
PROS:
Easy add-on to existing doors; provides good protection against tailgating and
piggybacking, unobtrusive in appearance, accommodates handicapped users, does
not require separate emergency exit, allows loading/unloading of large objects,
relatively inexpensive.
CONS:
Must be used at an entrance manned by security guard, does not provide good
visual and audible cues to users, some false alarms.
Comments:
Good choice for use at doorways with relatively low traffic volumes and where
conditions do not permit the use of another type of device.
VIDEO
ANALYTICS ANTI-TAILGATING SYSTEMS
Description:
Consists of video cameras installed at doorway opening. Cameras are connected
to a computer with special video analytics software that detects and analyzes
people and objects at the door. System may use multiple cameras that allow
precise determination of object size, height, and direction of travel. When
used at single door, video analytics anti-tailgating systems work similarly to
doorway anti-tailgating devices and sound alarm when more than one person
attempts to enter through door after a valid access card has been used. Video
analytics anti-tailgating systems can also be used with security portals to
both sound alarm and deny access when more than one person attempts to enter.
Approximate
cost: ₹ 3,50,000 per opening for single
door system, ₹ 12,50,000 to
₹ 15,50,000 for security portal system.
PROS:
Easy add-on to existing doors; provides good protection against tailgating and
piggybacking, unobtrusive in appearance, accommodates handicapped users, does
not require separate emergency exit, allows loading/unloading of large objects.
CONS:
Single door systems do not provide a physical barrier so must be used at an
entrance manned by security guard, requires frequent user training to prevent
false alarms, relatively expensive.
Comments:
Popular choice for use at computer rooms and other high-security facilities.
Selecting
the Right Anti-Tailgating System
Choosing
the right anti-tailgating system is an important decision. You need to consider
your overall level of security risk, your ability to provide security staff to
monitor your entrances and respond to alarms, and your budget for initial
purchase and ongoing maintenance of the anti-tailgating systems.
Artical Publish by Safe Secure Magazine in the month of May 2019 issue.