A guide to Access Control in the Retail sector
What is access control?
Access control provides the ability to
control, monitor and restrict the movement of people, assets or vehicles in,
out and around a building or site.
Access control is essential in the
protection of people and assets and has the additional benefit of being
expanded from controlling, for example, a single entrance door to a large
integrated security network.
There are also huge potentials in terms of
integrating access control with other systems, such as CCTV and intruder alarms, allowing for cost savings and
greater security benefits.
What risks does the retail sector face and
how can these be countered by access control?
The retail sector faces a variety of
threats all year round, including shoplifting, organised retail crime and
dishonest staff, and these risks can increase significantly during busy
shopping periods such as seasonal sales.
Recently, the BSIA carried out a survey of
its members to discover the trends in retail security over the last year. Over 50%
of respondents felt that the use of private security measures in retail had
increased over the past twelve months, with a further 65% anticipating this use
to increase over the course of the next year.
Members perceived the biggest threat to
retailers to be shoplifting and petty theft, with theft by employees following
in second. Online theft and armed robberies were also considered to be risks.
Retail environments are full of valuable
assets, both on the shop floor and in the stock room. Access control systems
are all designed to permit access only to people with the necessary authority
to enter a particular area, ensuring that goods and people are protected and
helping to manage known or anticipated threats.
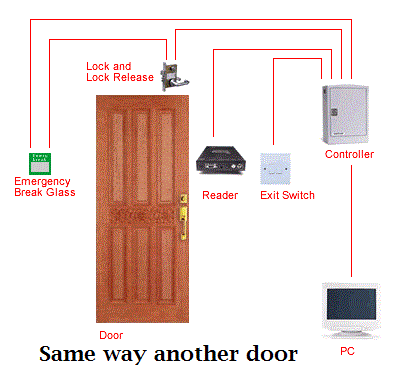
Generally, systems are comprised of three
main components:
1. The physical barrier – to physically
restrict access to a building or area. This can be achieved through methods
such as:
• Doors – secured
by either a magnetic or strike lock, or can be revolving or sliding.
• Turnstiles and speed
gates – designed to limit access to one person per identification device.
2. The identification device – there are a
number of different technologies available to identify users of an access control system, including:
• A proximity card
and reader via Radio-Frequency Identification (RFID) – these cards can be
programmed to work at a short or long read range
• A smart card and
reader
• A swipe card and
reader
• PIN pads
• Biometric
devices such as fingerprint or iris scanning
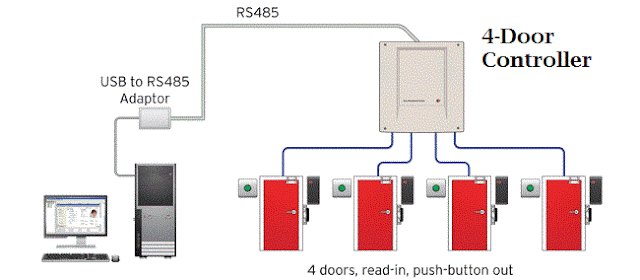
3. The door controller and software –
these are at the heart of the access control system and are used to decide who can gain access through which entry point and at what time of the
day are they permitted. These can vary depending on the size of the system and how many readers or sites you
are trying to control from one point. Some of the options include:
• A stand-alone
door controller linked to a single door with no software
• A number of door
controllers all linked together to a single PC to control one site
• A number of
sites all interlinked together over a wide network area
The added benefits of access control
Retail environments often incorporate
large numbers of staff working varied shift patterns. Access control systems
can offer a wide range of benefits, including Human Resource management and
integrated security systems.
Time and attendance
Retail security does not necessarily just
offer protection for the shop floor itself, but can encompass all stages of the supply chain – including staff offices,
warehouses and even the delivery process. Naturally, various different
employees and outside visitors are involved in these processes and access
control systems can assist with staff management.
Badge/token technology can be used to
record employee hours and monitor visitor movement within a specific site. If appropriate,
these can be processed against working hours, applicable for both temporary and
permanent staff – this can be useful for busy shopping periods when additional
seasonal staff are employed temporarily. This can work in real time to feed
transactions through to the company’s payroll. Time and attendance systems also
accurately help keep employers on the right side of the European Working Time
regulations and manage holidays and absences effectively. Fast, accurate and
easy-to-use, these systems are suitable for businesses employing just a few
people, right up to large multinational companies.
Automatic Number Plate Recognition
To monitor the movement of vehicles around
an area, CCTV-style cameras and computer software can be used to identify number
plates of vehicles. Some systems can also store photographs of the driver and
vehicle for subsequent analysis.
This sophisticated software allows
critical information to be passed to the police to assist in the pursuit,
identification and capture of offenders should an incident occur. For example,
if a shoplifter flees the scene of a crime via a vehicle, ANPR cameras situated
around an area could help identify the criminal. Visual proof of parking
offences with the corresponding time and date information is provided as evidence
and to avoid disputes. Using a Driver and Vehicle Licensing Agency (DVLA) link,
monitors are then able to identify the owner of a vehicle and process the
offence automatically.
Fire roll call
Health and safety is a key consideration
for any business. Since retail environments involve multiple staff members with
varying shift patterns, it can be difficult to keep track of all employees
during an emergency. Fire roll call technology generates a report containing
crucial information in relation to who is within the building and potentially
where they are. This software operates via the access control smart card or fob
that an employee uses to gain access to or exit a building. In the event of an
emergency, the fire roll-call software alerts occupants to the emergency whilst
simultaneously activating the report at a safe pre-determined remote point.
Please note: In order for the fire roll
call software to effectively carry out its function, employees and visitors
must always present their card or badge. The
use of smart card or RFID controlled turnstiles can help in this situation.
Integrated security systems
For maximum security, retail environments
can benefit from a fully integrated access control system with CCTV, intruder alarms,
fire detection and building management systems. One way to attain this is by
adopting the use of Internet Protocol (IP) technology, which allows these
systems to communicate with each other to maximise their effectiveness.
Separate access control and intruder alarm
systems, for example, could allow an employee to access an area that is set with
an alarm.
However, unless the employee has the
authority to unset the system, the access would result in a false alarm being activated – potentially causing panic in a
retail environment. An effectively integrated system would recognise that the user
does not have the authority to unset the system, so would not allow them in the
area to begin with.
What else should you know when considering
access control?
An initial risk assessment of an area can
determine the level of security required and subsequently influence the access control
system you choose. BSIA access control members and professional security
consultancies can assist with this.
BSIA members are subject to rigorous
checks before they are admitted into membership, meaning that you are selecting
a quality company. Below are just some of the reasons why BSIA members can
offer you peace of mind:
• They are
independently inspected to the quality standard ISO 9001 with a UKAS accredited
inspectorate
• They comply with
relevant British and European Standards and codes of practice
• Are financially
sound
• Professional
• Staff vetting
has been conducted where necessary
• They are
technically proficient and committed to quality training and development
• They are
up-to-date with the latest developments in British and European policy and
legislation
What legislation should you be aware of?
The Disability Discrimination Act was
amended in 2005 and has a significant impact not only in terms of the design of
new systems, but also means that many systems may need to be upgraded to ensure
compliance and adequate, user friendly access to the building for all staff and
visitors.
Other considerations to be aware of:
National minimum care standards
Health and Safety at Work Act
Occupiers Liability Act
Management of Health and Safety at Work Regulations.
Management of Health and Safety at Work Regulations.