Cyber threat into Video Surveillance
Yes we
all are known US ban HikVision, Dahua and IPVM media cover full story time by
time. Security systems are changing at an ever-increasing pace and are making
more use of standard Information Technology (IT) products running over a Local
Area Network (LAN) or Wide Area Network (WAN) e.g. across the Internet, where
they can be remotely monitored and controlled. As a result of using Internet
Protocol (IP), the opportunity has arisen for manufacturers to develop new
generations of equipment from control panels, cameras, and door controllers, to
fully integrated systems combining fire, access control, CCTV, intruder and
building control systems. These “integrated” systems are often called security
management systems as they bring together the management of all aspects of an organization’s
security.

Closed-circuit
television (CCTV) is a TV system in which signals are not publicly distributed,
but are monitored, primarily for surveillance and security purposes. CCTV
systems rely on strategic placement of cameras and observation of the camera’s
input on monitors. As the cameras communicate with monitors and/or video
recorders across private coaxial cable runs, or wireless communication links,
they gain the designation “closed-circuit” to indicate that access to their
content is limited to only those with authorisation to see it. First we need to
understand below few things:
What
is a network?
In
simple terms, a network provides a means of communicating data between two or
more computer-like devices. A network can be a LAN and can incorporate a
Wireless element of networking (WLAN). Where the network has the need to
communicate outside of a single LAN, a WAN is used. A WAN can connect LANs
together to communicate with users and computers in other locations. The most well-known
example of a WAN is the Internet.
Why
use an IP network?
Traditionally,
many security systems have been linked to remote monitoring centres using modem
type devices connected to a telephone line to exchange information. Using a
network introduces many benefits, for example a substantial financial saving
compared to dial up solutions. Additionally, the use of a network can improve quality
of information and the time required to connect and exchange information.
Digital
formats are being chosen by many industries such as music, telephone (voice
over IP networks), TV, photography etc. With so many industries making use of
IP technology, networks have become extremely robust. As a result, the use of a
network can make the exchange of information between a security system and a
remote monitoring centre more efficient.
Internet
Service Provider (ISP)
The
connection between your premises and the monitoring location may use an ISP to
provide the service. When choosing an ISP, you should endeavour to establish
the level of service being offered. Additionally, it may be prudent to have a
second ISP link. The connection between your premises and the ISP is perhaps
the weaker link so if you do have concerns, you should investigate an alternate
means of communication from your premises into the ISP, i.e. GPRS, GSM (mobile
service providers).
Bandwidth
Bandwidth
requirements (space on your network to operate) should be discussed with your
IT manager. The bandwidth required to operate a CCTV system may be
considerable. Your security system provider will be able to advise you on the
bandwidth requirements. As a general guide, CCTV systems require considerable bandwidth
to send video images over a network whereas access control, intruder alarm
systems and visitor management systems that only send small amounts of data, do
not require much bandwidth.
Company
usage policies
You will
also need to consider company policies relating to “what is allowed” to use an
existing network. If the nature of your business dictates that the network
shall only be used for specific applications, then this may immediately
determine that a separate network must be installed for the security system.
Now SSA
Integrate company Integrating existing security with IP security solutions. As
now common backbone are under TCP/IP. The network of connected sensors,
devices, and appliances commonly referred to as the Internet of Things (IoT)
has completely changed the way business works. This is as
true of
the heavy hauling and freight industry as any other. At any moment, various
players in the industry can get a sense of vehicle health, cargo safety, and
whether or not any infrastructure is in need of repair.
Some
products allow a mixture of analogue and digital security equipment to be
combined, and this means that there is not always a need to move completely to
an IP based system if an existing security system is in place.
The
‘hybrid’ approach is more common where two or more security sub systems are
combined to create an integrated solution. The data in a hybrid system will
usually come together at one or more PC’s. Non-IP systems are often connected
to a PC using a serial port, whereas IP systems will be connected over the
network.
A
cyber-attack at targeted points in a country or region’s network could leave it
crippled, preventing people from receiving much-needed goods and services. Fortunately,
it doesn’t have to be that way.
Now
cyberattacks on CCTV systems making news headlines on a weekly basis of late,
there is a good deal of concern and uncertainty about how at risk these systems
are, as well as why they are being attacked.
In
October 2016, 600,000 internet connected cameras, DVR’s, routers and other IoT
devices were compromised and used to for a massive Bot Net to launch what was
the largest Denial Of Service (DOS) attack the internet had experienced to date.
In 2014,
a US ally observed a malicious actor attacking the US State Department computer
systems. In response the NSA traced the attacker’s source and infiltrated their
computer systems gaining access to their CCTV cameras from where they were able
to observe the hackers’ comings and goings.
In the
lead up to the 2017 US Presidential inauguration, 65 per cent of the recording
servers for the city of Washington CCTV system were infected with ransomware.
How did the attack take place? Whilst unknown, it most likely occurred by the
same means as other common PC hacks such as infected USB keys, malicious web
sites, or phishing attacks.
What was
the impact? The system administrators had to wipe the infected systems and
reinstall the video management system so it’s entirely possible a good deal of
footage was lost, and the system was rendered inoperable for a time.
May,
2018, over 60 Canon cameras in Japan were hacked with “I’m Hacked. bye2”
appearing in the camera display text. How did the attack take place? Simple.
IP cameras were connected to the internet and were left on default credentials.
It appears that the hackers logged into the cameras and changed the on-screen
display. What was the impact? Other the defacement of the camera displays and
some reputational damage, there doesn’t seem to have been much impact from
these attacks.
How did
the attack take place? Yet again, devices were left connected to the internet
and were left on default credentials. In this case, the attackers developed
software that scoured the internet searching for vulnerable devices, which they
then took control using their own malicious software.
What
lessons can we learn from these attacks?
Don’t
connect your devices directly to the Internet. If you need to have a camera or
CCTV system be remotely accessible, port forwarding all inbound traffic to your
system is just asking to be attacked. Use a VPN, use non-standard network
ports, enable 2 factor authentications, or use a remote access service. While
these measures won’t guarantee your security, they will certainly make you less
of a target for attackers that are scouring the internet for vulnerable
systems.
Just
because it connects to a bunch of cameras, doesn’t mean that your NVR isn’t a
computer. All the cyber security advice that is applicable to traditional IT is
just as applicable when said computer is used as part of a CCTV system.
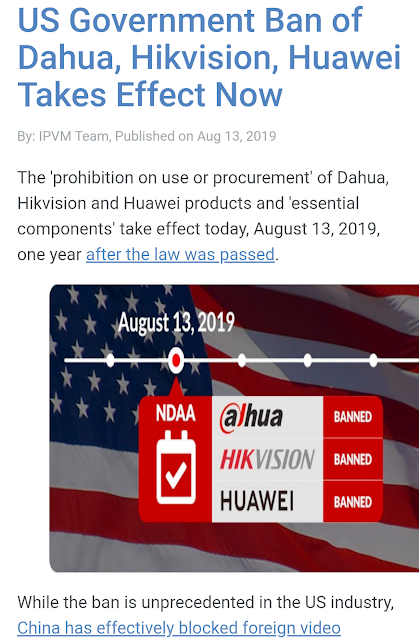
On Aug
13, 2018, The US President has signed the 2019 NDAA into law, banning the
use of Dahua and HikVision (and their OEMs) for the US government, for US
government-funded contracts and possibly for 'critical infrastructure' and
'national Security’ usage.
US
government is effectively blacklisting Dahua and HikVision products, this will
have a severe branding and consequentially purchasing impact. Many buyers will
be concerned about:
·
What
security risks those products pose for them
·
What
problems might occur if they want to integrate with public / government systems
·
What
future legislation at the state or local level might ban usage of such systems
On Jun
06, 2019 Hanwha Techwin is dropping Huawei Hisilicon from all of their
products. Its belongs to China’s origin. Backdoor entry are open on product.
The
tightening noose around Chinese technology firms is driven by the Trump
administration’s view that China poses an economic, technological and political
threat, a stance that country is likely to retaliate against. The two companies
prompted concern that they could be employed in espionage, according to
people familiar with the matter. Last week, the administration
banned Huawei Technologies Co. from purchasing American technology amid
similar suspicions of spying capabilities and Chinese laws that could require
home-grown firms to hand over information if asked.
Hikvision,
which is controlled by the Chinese government and Dahua are leaders in the
market for surveillance technology, with cameras that can produce sharp,
full-color images in fog and near-total darkness. They also use artificial
intelligence to power 3D people-counting cameras and facial recognition systems
on a vast scale.
A
Chinese firm whose subsidiary has been shortlisted to supply security cameras
for the national capital is on a US watch list, with an advisory on threats,
including remote hacking and potential backdoor access.
Concerns have also been raised on the firm being owned by the Chinese
government, adding a twist to the controversy over a Delhi government project
to install 1.5 lakh CCTV cameras across the city. Now question is how you Prevent
Malware Attacks:
1. Manage your router: Earlier this
year, the FBI recommended that everyone reboot all home routers and small office
routers. In a previous blog on the subject, Davis stated that “rebooting will
disable the active malware called “VPN Filter" which has infected hundreds
of thousands of routers across the Internet, and it will help the FBI assess
the extent of the infection.” While this was an isolated incident in time,
2. Disable UPNP: UPNP will
automatically try to forward ports in your router or modem. Normally this would
be a good thing. However, if your system automatically forwards the ports, and
you leave the credentials defaulted, you may end up with unwanted visitors.
3. Disable P2P: P2P is used to remotely
access a system via a serial number. The possibility of someone hacking into
your system using P2P is highly unlikely because the system’s user name,
password, and serial number are also required.
4. Disable SNMP if you are not using
it. If you are using SNMP, you should do so temporarily, for tracing and
testing purposes only.
5. Disable Multicast: Multicast is used
to share video streams between two recorders. Currently there are no known
issues involving Multicast, but if you are not using this feature, you should
disable it.
6. Cameras connected to the POE ports
on the back of an NVR are isolated from the outside world and cannot be
accessed directly.
7. Only forward the HTTP and TCP ports
that you need to use. Do not forward a huge range of numbers to the device. Do
not DMZ the device's IP address.
8. Protect your computer from
vulnerabilities: Clean up your computer by removing old software programs no
longer in use, and make sure to install patches regularly. Updating firmware
safeguards equipment by patching known vulnerabilities often adds features and
sometimes will improve system performance.
9. Use firewalls and firebreaks
(network segmentation): Place devices behind firewalls to protect them from
untrusted networks, such as the Internet. And, use network
segmentation—splitting a network into separate networks that are isolated, not
connected—so a compromise in one part of the network won’t compromise the other
(i.e. human resources and finance). This works much like a firebreak, which is
a strip of land in a wooded area or forest where the trees have been removed to
prevent a fire from spreading.
10. The
network your NVR and IP camera resides on should not be the same network as your
public computer network. This will prevent any visitors or unwanted guests from
getting access to the same network the security system needs in order to
function properly.
Some
Protection Protocols:
Cyber security procedures for video surveillance devices across the threat spectrum require
certain protection protocols.
Weaponizing
IP Cameras (Threat High)
Most IP
cameras today are manufactured with an open operating system, or basic kernel,
that gives no real consideration to data or cybersecurity. For years, people
have asked about the security of the video that their system produces; now,
people are asking if their IP camera system can be used against them.
Think of
an IT administrator who has worked diligently to secure a network, servers and
mobile devices who then finds out that the 200 recently installed IP cameras on
the edge of that network that are vulnerable to root kits, can be weaponized
and used as attack platforms against their own network – and there is no way to
monitor them.
This may
seem far-fetched, but in Sept. 2016, 1.5 million IP cameras, DVRs and L3
network devices were highjacked in the largest DDOS attack ever seen. So what
are the current fundamental considerations that an organization needs to take
into consideration before placing an IP camera on their network?
Protection
Protocol:
·
The
operating system (OS) on a video device should be a closed OS that runs in
limited memory space.
·
Nothing
should be able to be written to the device itself with the exception of
digitally signed firmware. If the device has the ability to run third-party
apps, it can be weaponized.
·
Common
ports should be disabled by default. From a vulnerability and pen testing
perspective, the more ports that are open, the more opportunity there is to
leverage a device or the services on that device.
·
Video
devices should utilize HSTS/ HTTP Strict Transport Security if you are going to
implement end-to-end security. This protocol helps protect against protocol
downgrade attacks, cookie high jacking, as well as forces an HTTPS connection
to the device.
·
Consider
devices with a built-in “firewall” to prevent dictionary attacks from Botnets.
·
Monitor
user accounts and access to the video devices. Most IP cameras are installed
with the default user name and password, and if installed on an accessible
network, a connection can be established from anywhere in the world. Devices should
have a force password feature that also adheres to password policies, such as
length and complexity.
·
Monitor
a device’s chain of custody. The vendor should have a secure chain of custody
during a manufacturing process all the way through to the final sale. If they
are not manufactured in a controlled environment, video devices can be tampered
with at any time prior to being sold to the customer
Attacking
Servers and NVRs (Threat High)
Most VMS
servers and NVRs reside on either a Windows operating system or some flavor of
Linux. There is an illusion of security that most of us have with regards to OS
security, but just take a look at an OS vulnerability chart and that illusion
will quickly disappear.
A base
unpatched Windows Server 2012 OS has 36 vulnerabilities; a standard Linux
distribution has 119. Most vulnerability that machines are subject to are a
result of “add-ons” – such as Internet Explorer (242) and Chrome (124). While
Windows Server is a more secure platform, it is also a bigger target due to its
market share and utilization.
Protection
Protocol:
·
As
with any machine on a network, it is imperative that the most current updates
and patches are applied to video system devices.
·
Ensure
a VMS can work within your network policies and environment while a network
firewall and anti-virus software are operational.
·
Use
hardened password policies, restricted physical and network access, and disable
USB ports.
Recorded Video
(Data at Rest-Threat Medium)
The two primary
purposes of any video system are to act as a deterrent and to be used as
admissible evidence in a court of law, if needed. Technically, digital video
falls under the scrutiny of the Federal Rules of Evidence (FRE) as it pertains
to digital evidence, and authenticity affects admissibility.
Most NVR
systems write video in a base file format such as *.AVI,*.G64, *.MKV. If the
video drives are accessible via network share, they are subject to tampering.
Protection Protocol:
·
Video,
if written in a readable format, should be encrypted to reduce accessibility
and the possibility of tampering.
·
Video
devices should use some form of hashing as a form of authenticity. Hashing
provides the “Data Fixity” of a file and is a form of admissible evidence. Older
forms of authenticity, such as water marking can be considered video tampering.
·
The
VMS should also provide a way to protect original incident video for any
undefined time beyond the system’s retention time in case of prolonged court
cases.
Playback and Export
(Data in Use-Threat Medium)
The
current biggest threat to recorded video is internal employees posting incident
video footage to social media or leaking it to the press. The need to keep
recorded video secure is paramount for many reasons. Unrestricted access to
recorded video can cause several different types of issues, including legal and
HR incidents.
Protection Protocol:
·
Be
sure your VMS provides granular privileges concerning the export, deletion and
protection of recorded video.
Streaming Video
(Data in Motion-Threat Low)
While
the actual threat of streaming video being intercepted and used in some way is
low, the knowledge that the data from a specific IP address is video can be
used against you. From the aspect of network enumeration, an attacker now knows
he has non-PC target(s) that he can try to leverage.
Protection Protocol:
·
Video
devices should be able to utilize HTTPS communications, with certificates. This
ensures secure end-to-end communications including control channels and video
payload.
·
Video
devices should be equipped with a Trusted Platform Module (TPM) to securely
store certificates utilized in different secure network scenarios such as
802.1x and Public Key Infrastructure (PKI).
·
Your
video devices should have features that provide the ability to disable certain
protocols such as ICMP, Telnet, and FTP.
3. IPVM
Report