Do you need
an Access Control Systems?
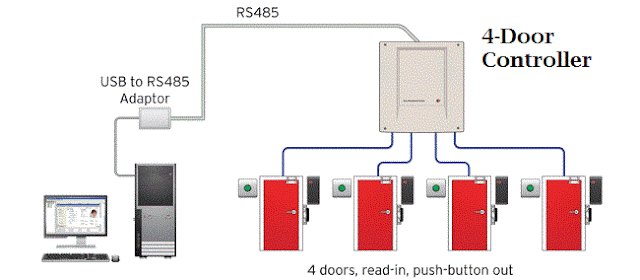
Design 3: 4-Door single controller.
Design 4: New Concept, PoE Based
Design 5: SYRiS Product with SQL Database, Multi-location. One SY230NT Controller can controll 4nos of Door. Practically i do many projects with this.
Access control security systems are designed to restrict
physical entry to only users with authorization. Many organizations,
governmental and private, have started adopting access control security systems
for physical entry into their facilities. Whether it is a simple non
intelligent access control system like a punching in a password, or advanced
biometric systems that scan and permit entry very specifically, there are many
advantages to employing these security systems.
It is important for businesses of every size to keep important data and remove threats. All businesses acknowledge this basic security concern by placing locks on the door and giving keys to employees that need to access these locks. If you answer yes to any of the following questions, you may need access control systems:
It is important for businesses of every size to keep important data and remove threats. All businesses acknowledge this basic security concern by placing locks on the door and giving keys to employees that need to access these locks. If you answer yes to any of the following questions, you may need access control systems:
- Is a lost or stolen key a security threat to your
business?
- Time Based Control for Security Systems
- Do you need different access for different employees
and clients?
- Would it be really beneficial to restrict access based
on time or day?
- Do you need a record of people’s “comings and goings?
- Could your employees/clients be more secure?
- Reduced Requirement for Manpower
- Biometric Systems
- Is a lost or stolen key a security threat to your
business?
Benefits of
access control systems
The benefits of access control systems are thus many:
- Audit trail –
With access control systems, you will have a record of every opening and
attempted opening of each door or specific area. The audit trail can be
valuable in resolving employee issues.
- Time/day restrictions –
Do you have certain employees that should only be there at certain times
and days. An access control system make more sense to control their access
than to give them a key that allows access at any time or day.
- Lost or stolen keys –
When keys are lost or stolen, it is an expensive process for a business to
completely rekey each door. Access control systems allow you to remove
access by deactivating the I.D. badges or other security credentials.
- Remote access control –
Many access control systems allow you to control of all of the business’
locks from one main system. With access control systems, you can easily
and quickly lock down your businesses in an emergency as well as add and
remove credentials.
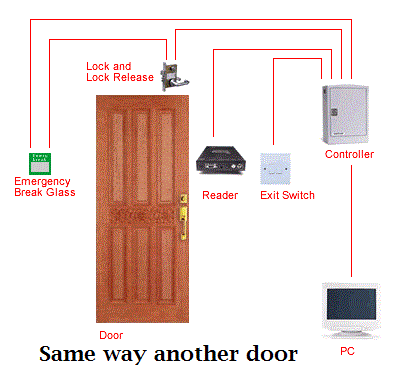
Design 1:
Design 2: Single DoorDesign 3: 4-Door single controller.
Design 4: New Concept, PoE Based
Design 5: SYRiS Product with SQL Database, Multi-location. One SY230NT Controller can controll 4nos of Door. Practically i do many projects with this.
How the Access Control System
WorksØ The typical access control system
consists of a card/ pin reader, electromagnetic lock or door strike, power
supply system and a push button.