Biometrics Systems usage and Advantages
Biometrics Systems are spreading its limbs in
almost every sector, as it ensures security to the top most level. Looking at
its multidimensional features, biometric systems are used for various
applications.
In today's technologically modern era, the biometric systems are replacing
other conventional methods for different purposes. Biometrics Systems can be
used to-- Manage Attendance, Access Control, Leave Management, Payroll
Processing and many more. This really helps to optimize the solutions according
to one's requirement. These solutions help to reduce the chaos of work and also
reduces administrative costs.
How secure Biometric Systems are?
Biometric features of each individual are unique in itself, which cannot be
tampered or manipulated. Though there are few possibilities to break the
security, so to manage optimum security level, biometric systems can be secured
with passwords and PIN codes.
How Biometrics Systems are beneficial?
Biometrics systems
are useful in many ways, and its benefits depend on the application. Following
are the most important benefits of biometrics systems which can help any firm
to streamline the work force:-
Reduces Time and other paper works
Biometric solutions
can easily reduce the time consumed in hectic calculations and paperwork
required in salary processing or other processes. Now these solutions generate
reports easily. The reports can be generated monthly or weekly or daily;
depending on the requirements.
Accurate Identification
While traditional security systems are reliant on passwords,
personal identification numbers (PINs) or smart cards, you can achieve a high
level of accuracy with biometrics systems. If you have set up the system
correctly, you can use biological characteristics like fingerprints and iris
scans, which offer you unique and accurate identification methods. These
features cannot be easily duplicated, which means only the authorized person
gets access and you get high level of security.
Reduces Human efforts and administrative costs
Since each report is easily generated, so there is no requirement of
involvement of more than one employee. Also, each and every detail of each
employee is managed easily, thus there is no chance of any kind of
manipulation. This reduces the administrative costs.
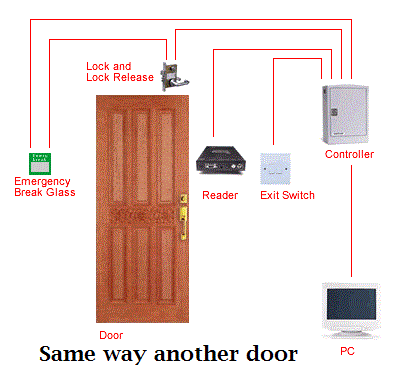
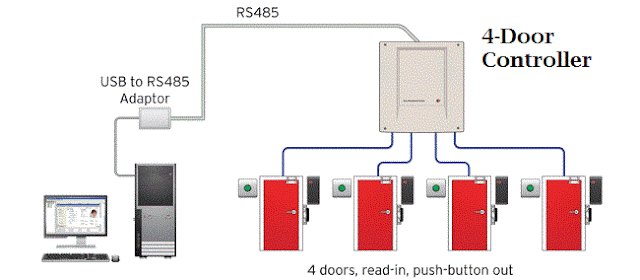
Restricts unauthorized access
The Access
Control Solutions are generally used to restrict the unauthorized
movements of any person. It basically works on biometrics of an employee. It
also allows to limit the access of employees to a certain range of the office
premises.
Accountability
Biometric log-ins
mean a person can be directly connected to a particular action or an event. In
other words, biometrics creates a clear, definable audit trail of transactions
or activities. This is especially handy in case of security breaches because
you know exactly who is responsible for it. As a result you get true and
complete accountability, which cannot be duplicated.
Helps to maintain attendance and other records
The Biometric Systems can be used to maintain the attendance of each
employee and also manages other records, including OTs, Leaves, etc. A report
of records can be generated according to the requirements.
Different solutions based on biometrics for
different purposes
Biometric systems can be linked with different solutions like leave
management system, canteen management system, payroll software and time office
software to solve different purposes.
Security
Another advantage these systems have is that they can’t be
guessed or stolen; hence they will be a long term security solution for your
company. The problem with efficient password systems is that there is often a
sequence of numbers, letters, and symbols, which makes them difficult to
remember on a regular basis. The problem with tokens is that they can be easily
stolen or lost – both these traditional methods involve the risk of things
being shared. As a result you can’t ever be really sure as to who the real user
is. However that won’t be the case with biometric characteristics, and you
won’t have to deal with the problem of sharing, duplication, or fraud.
Scalability
Biometrics systems can be quite flexible and easily
scalable. You can use higher versions of sensors and security systems based on
your requirements. At the lowest level you can use characteristics that are not
very discriminative; however if you are looking for a higher level of security
for large scale databases then you can use systems with more discriminable
features, or multi-modal applications to increase identification accuracy.
Convenience
It’s considered to be a convenient security solution
because you don’t have to remember passwords, or carry extra badges, documents,
or ID cards. You are definitely saved the hassle of having to remember
passwords frequently or changing cards and badges. People forget passwords and
ID cards are lost, which can be a huge nuisance with traditional security
methods.
Versatility
There are different types of biometrics scanners available
today and they can be used for various applications. They can be used by companies
at security checkpoints including entrances, exits, doorways, and more.
Moreover you can make the most out of the biometric
solutions to decide who can access certain systems and networks. Companies can
also use them to monitor employee time and attendance, which raises
accountability.